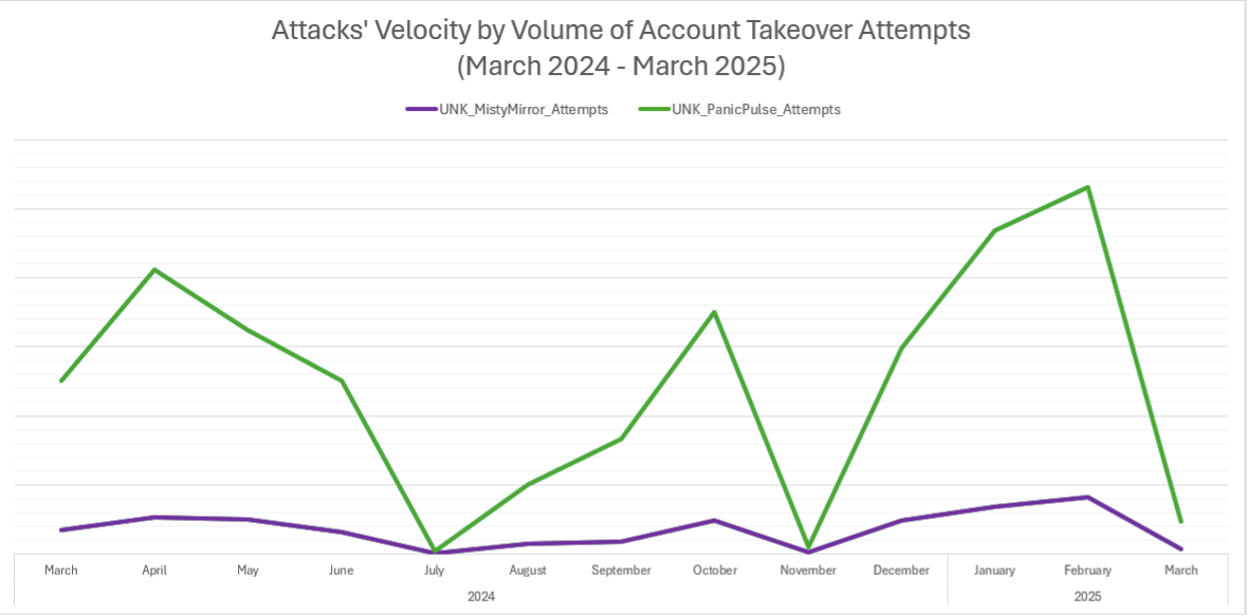
Proofpoint researchers have identified two active #accounttakeover (#ATO) campaigns, tracked as UNK_PanicPulse & UNK_MistyMirror, targeting #Microsoft365 accounts.
Since March 2024, both clusters have affected 6K+ accounts across 1.4K+ organizations, using botnets & unique client agents.
Our threat analysts have found strong similarities between these threat clusters’ operational infrastructure, tactics, and target selection methods, suggesting that these wide-scale, botnet-driven ATO threats may be tied to a single (currently unattributed) threat actor.
---
Key TTPs:
• Password spraying – Using generic passwords across multiple accounts
• IP rotation – 2.9K IPs linked to 30 abused proxies & ISPs
• Distinct client agents – Leveraging known web crawlers & RSS fetchers
• ‘O365 Suite UX’ abuse – Targeting M365 native sign-in app
---
IOCs (observed user agents):
• AdsBot-Google
• Bloglines/3.1
• FeedFetcher-Google
• Gaisbot/3.0
• msnbot/0.11 & 1.1
• Peach/1.01 (Ubuntu 8.04 LTS)
• facebookexternalhit/1.1