MITRE has assigned two CVEs for @micahflee’s #vulnerability findings on TM SGNL (the weird hacked up version of #Signal from TeleMessage that some high-ranking USG people use).
https://www.cve.org/CVERecord?id=CVE-2025-47730
tags: #signal #vulnerability
to: https://infosec.exchange/users/micahflee
The Perl 5 Porters have released #Perl versions 5.40.2 and 5.38.4 to address CVE-2024-56406. It is believed that this #security #vulnerability can enable Denial of Service or Arbitrary Code Execution attacks on platforms that lack sufficient defenses.
You can soon download both from your favorite #CPAN mirror or find them at:
https://metacpan.org/release/SHAY/perl-5.40.2/
https://metacpan.org/release/SHAY/perl-5.38.4/
Changes are listed in their respective “perldelta” documents:
https://metacpan.org/release/SHAY/perl-5.40.2/view/pod/perldelta.pod
🚨 March 12 UPDATE: Grafana Exploitation May Signal Multi-Phase SSRF Attacks. Update + original analysis:
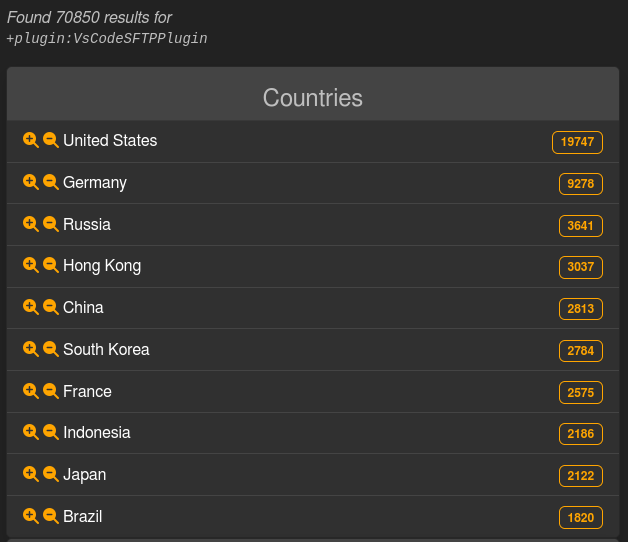
⚠️ During our scans we found ~70K applications exposing their VSCode SFTP config.
These are often critical and can include FTP/SSH credentials.
You can check this out here: https://leakix.net/search?q=%2Bplugin%3AVsCodeSFTPPlugin&scope=leak
All videos from The 38th Chaos Communication Congress (38C3) 2024: