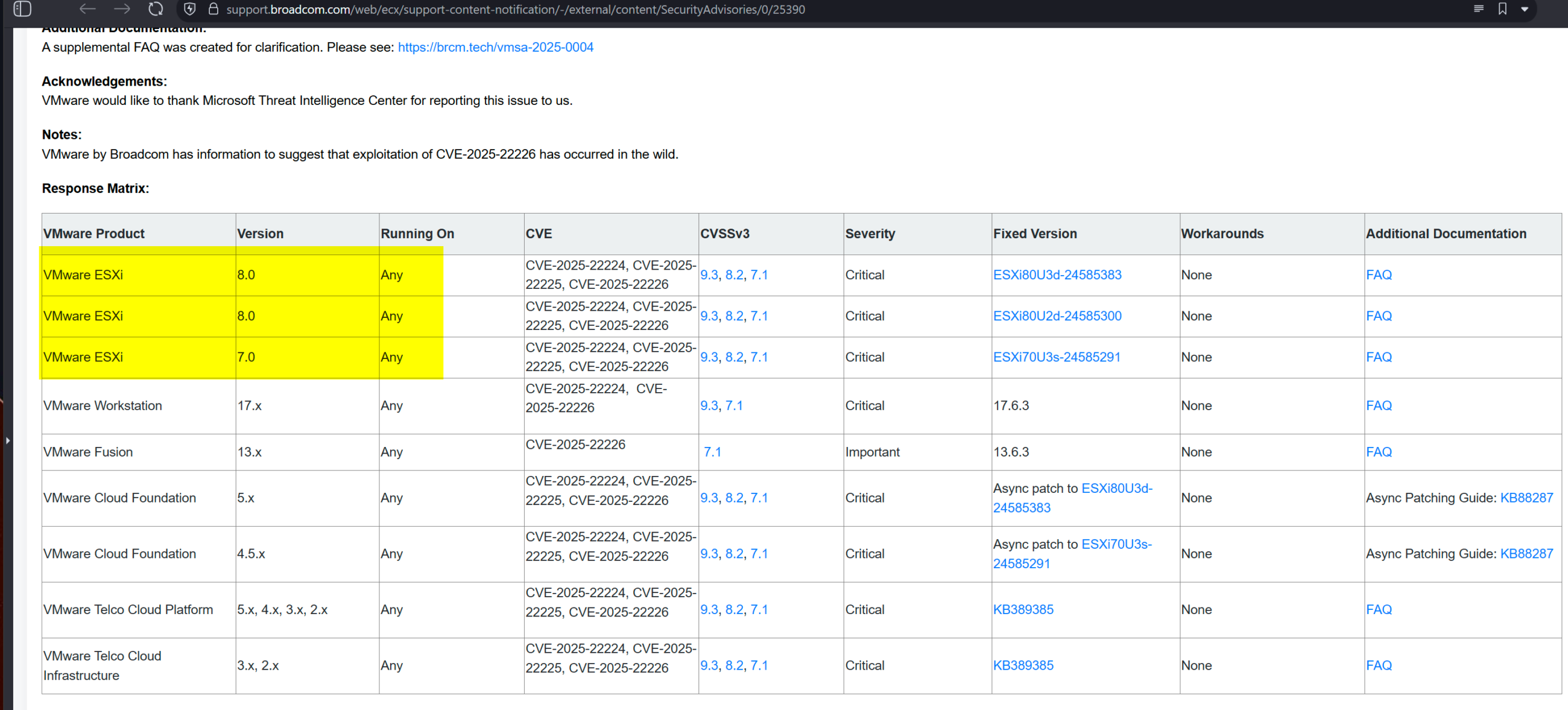
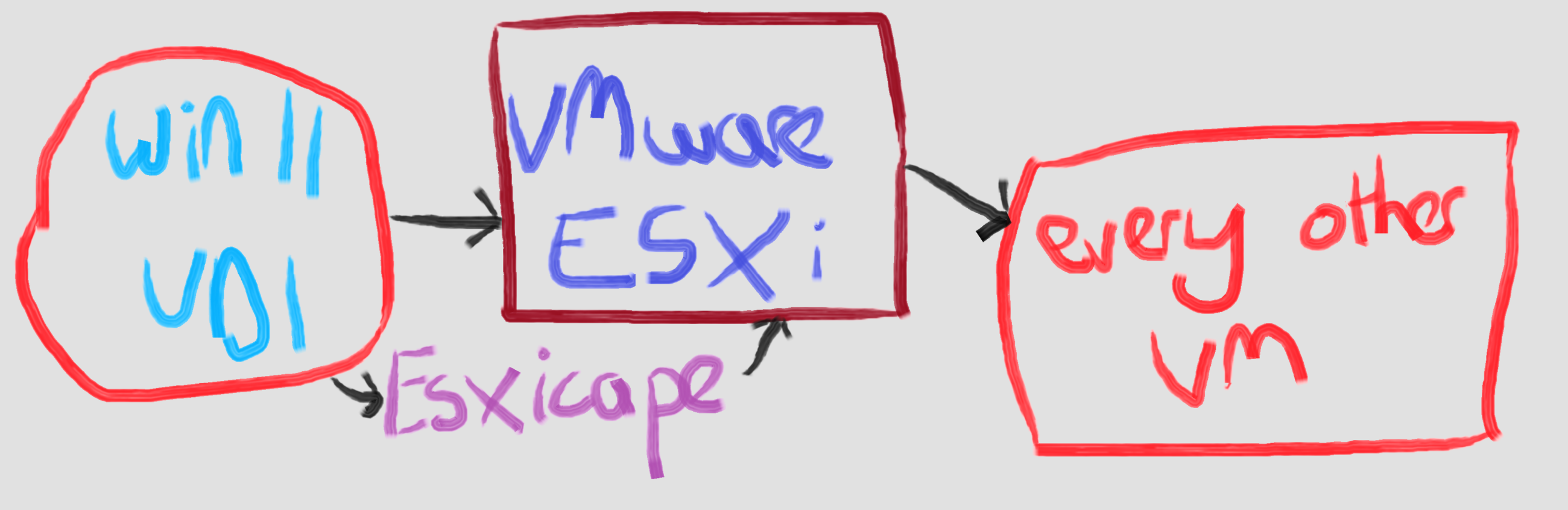
A new twist on #ESXicape - you need local admin rights to escape the VM to the hypervisor, right?
Slight issue - VMware Tools, installed inside VMs, allows local user to local admin privilege escalation on every VM due to vuln CVE-2025-22230
“A malicious actor with non-administrative privileges on a Windows guest VM may gain ability to perform certain high-privilege operations within that VM.”
Discovered by Positive Technologies, who US claim hack for Moscow.