Write up on the LockBit hack https://www.bleepingcomputer.com/news/security/lockbit-ransomware-gang-hacked-victim-negotiations-exposed/
Somebody has hacked LockBit. I’m going to guess DragonForce. They’ve dumped their victim payment chats and backend SQL.
Masimo, the e-watch maker, has filed an 8-K with the SEC for a ransomware incident.
They don’t say ransomware, but it is.
Their website was down for 5 days, including investor relations, along with all their customer support numbers and online systems. They quietly fixed the website, then filed with the SEC. https://www.sec.gov/ix?doc=/Archives/edgar/data/937556/000110465925045035/tm2514064d1_8k.htm
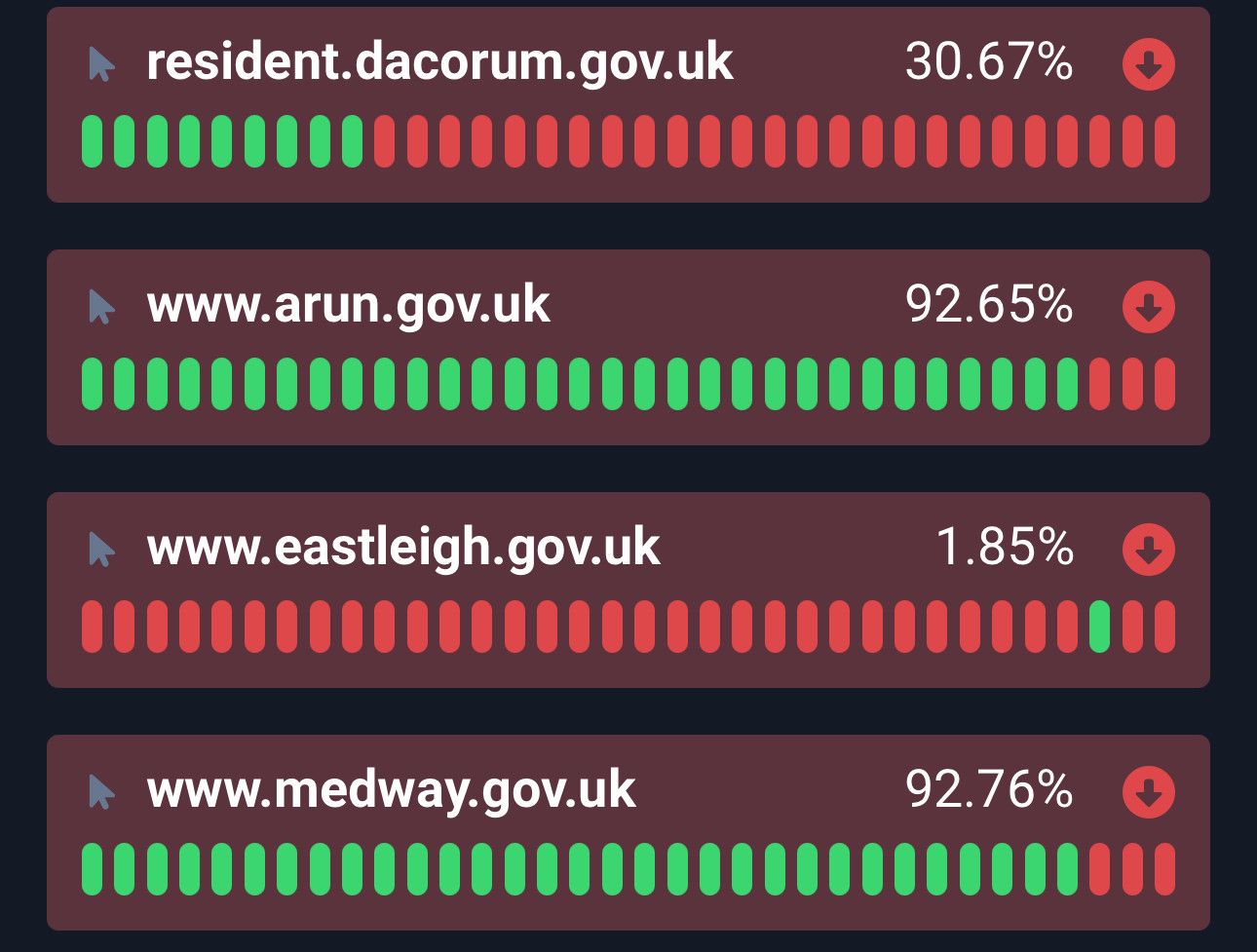
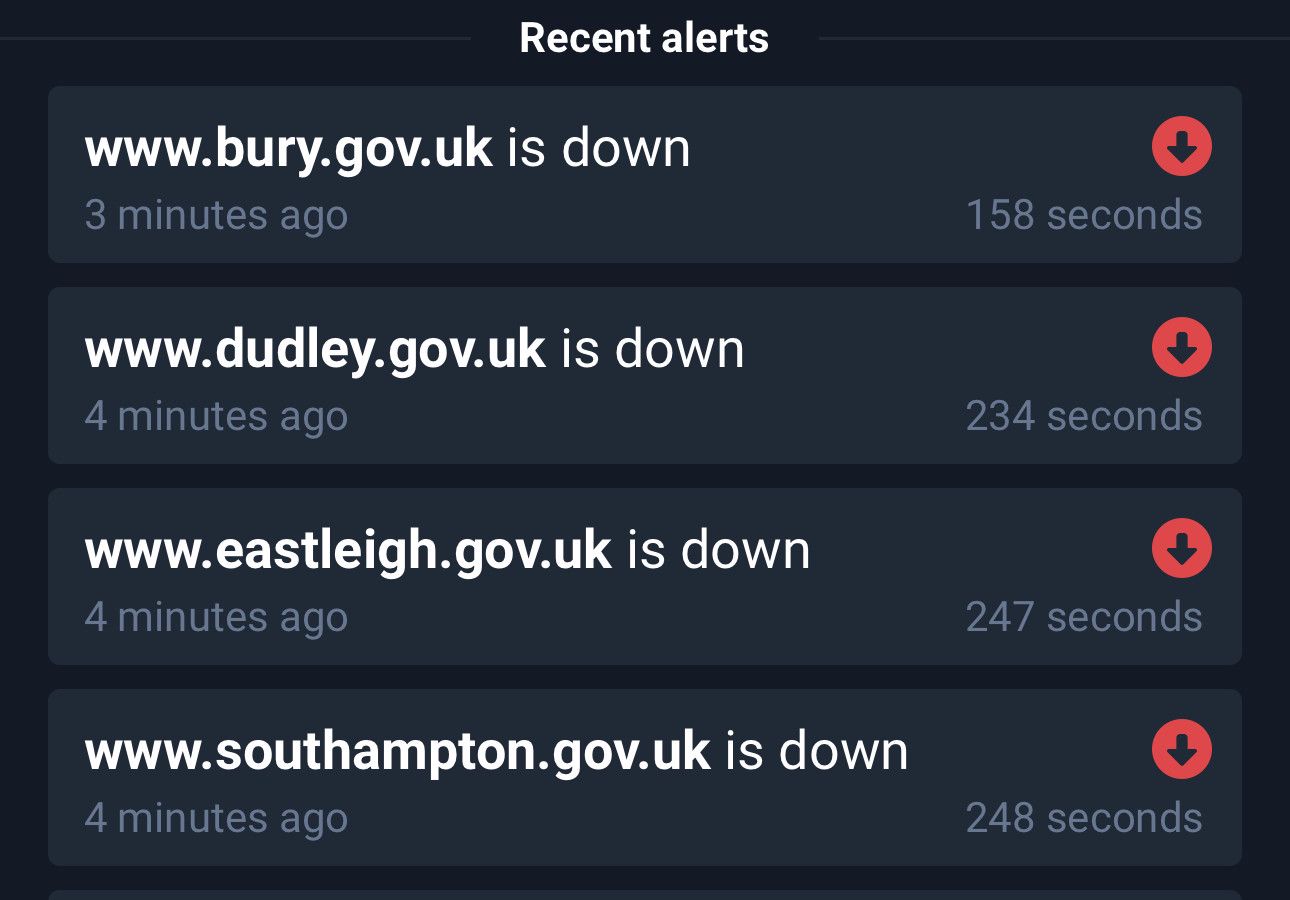
NoName continue UK targeting.
Botnet config: https://witha.name/data/2025-05-06_07-10-03_DDoSia-target-list.csv
#NoName are back targeting UK councils. Same config as prior UK runs.
Botnet config: https://witha.name/data/2025-05-05_08-20-03_DDoSia-target-list.csv
One of M&S’ biggest suppliers have said they have reverted to pen and paper for orders due to M&S lacking IT.
Additionally, M&S staff are raising concern about how they will be paid due to lack of IT systems.
M&S are over a week into a ransomware incident and still don’t have their online store working.
https://www.bbc.com/news/articles/cvgnyplvdv8o
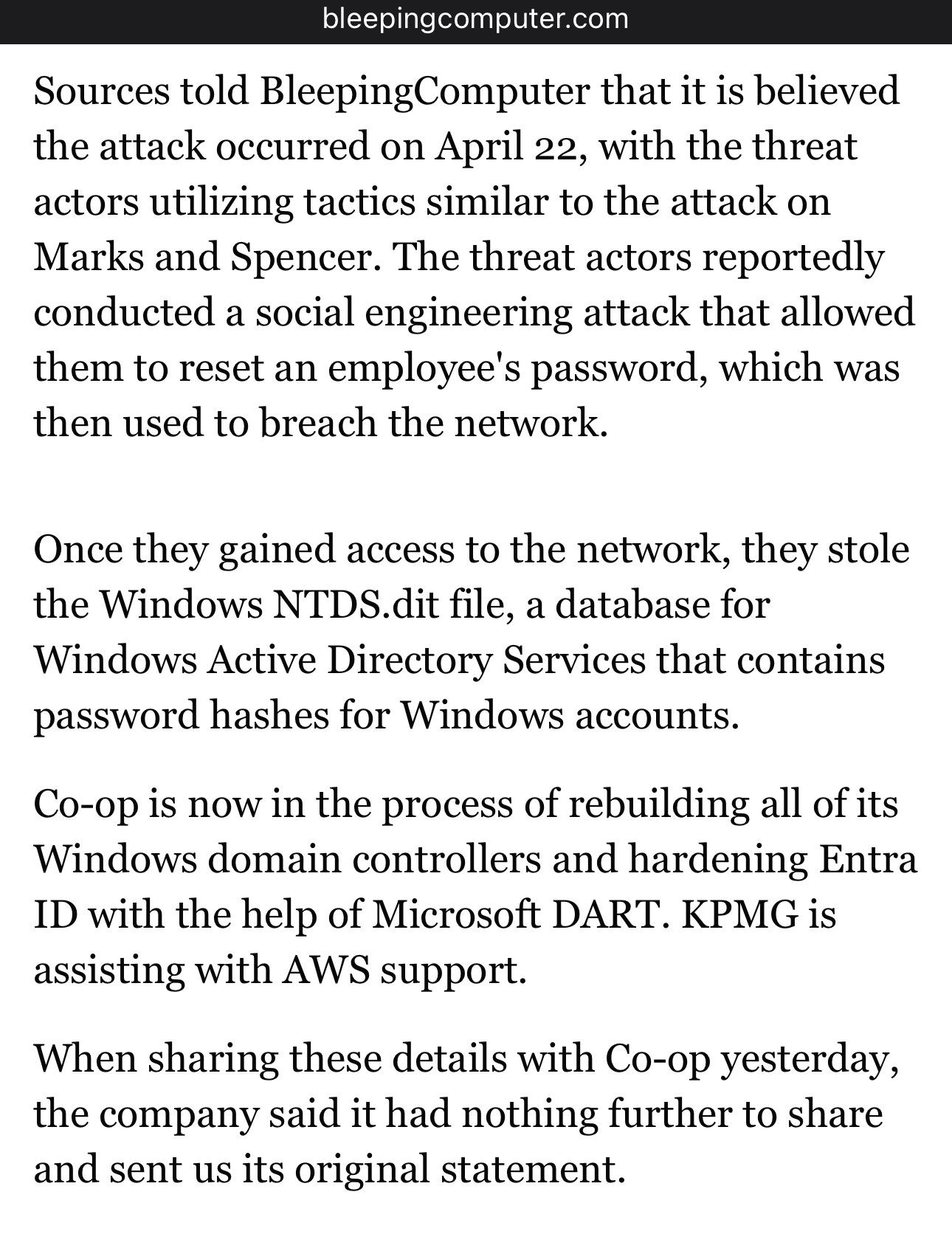
Bleeping Computer have more on the Co-op breach https://www.bleepingcomputer.com/news/security/co-op-confirms-data-theft-after-dragonforce-ransomware-claims-attack/
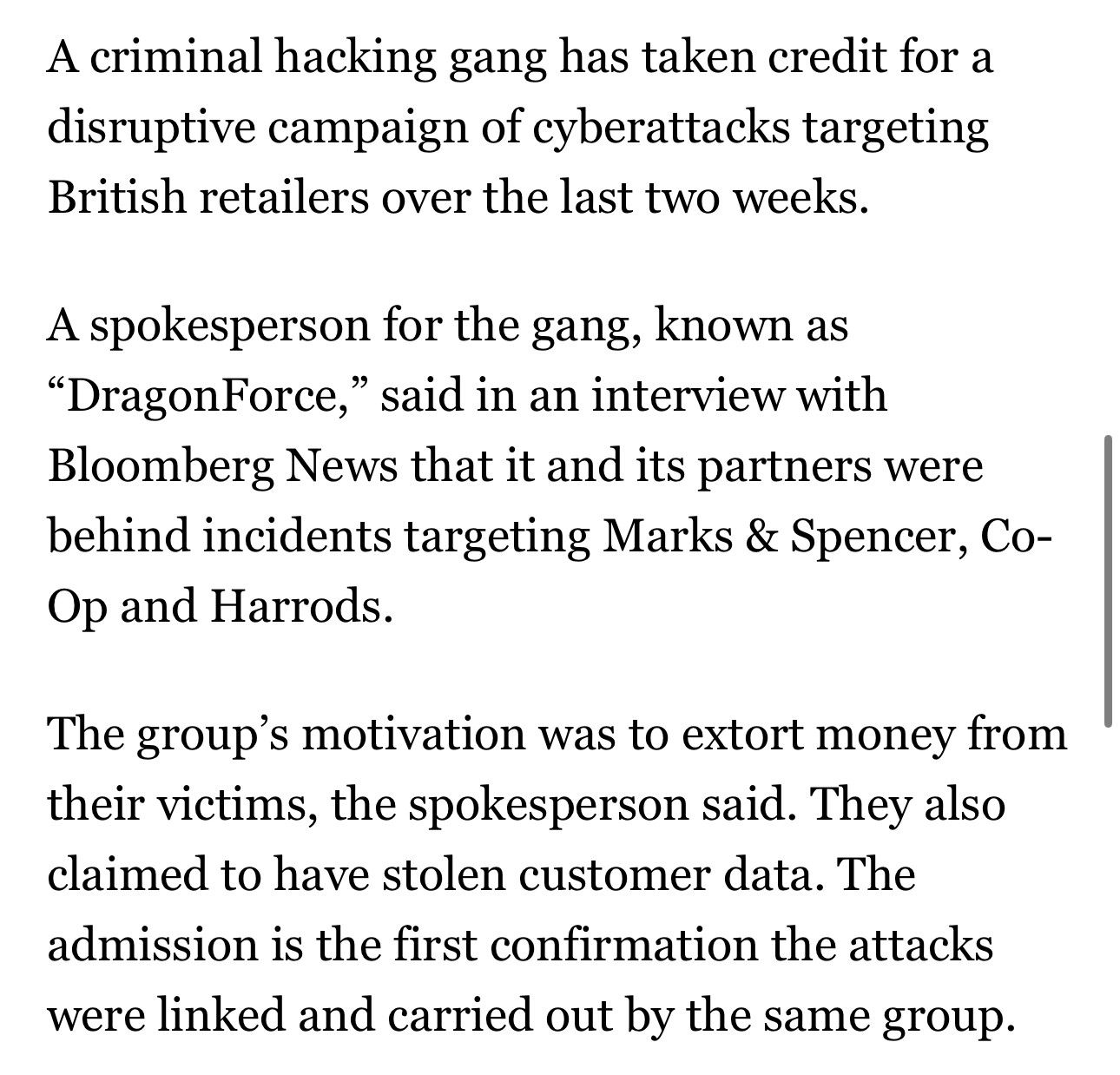
DragonForce Ransomware Cartel are claiming credit for attacks on Marks and Spencer, Co-op and Harrods and say more victim orgs are coming https://www.bloomberg.com/news/articles/2025-05-02/-dragonforce-hacking-gang-takes-credit-for-uk-retail-attacks
tags: #cybersecurity #infosec #threatintel
to: https://infosec.exchange/users/ESETresearch
OH! I did not realize @ESETresearch was on Mastodon!
They do *fantastic* security and threat research. Highly recommend you follow 'em and/or add them to your RSS reader.
Harrods becomes latest retailer to have a cyber incident, after M&S and Co-op Group. https://news.sky.com/story/luxury-store-harrods-is-latest-retail-victim-of-cyber-attackers-13359363
Cyber Toufan appear to have got the hots for Microsoft.
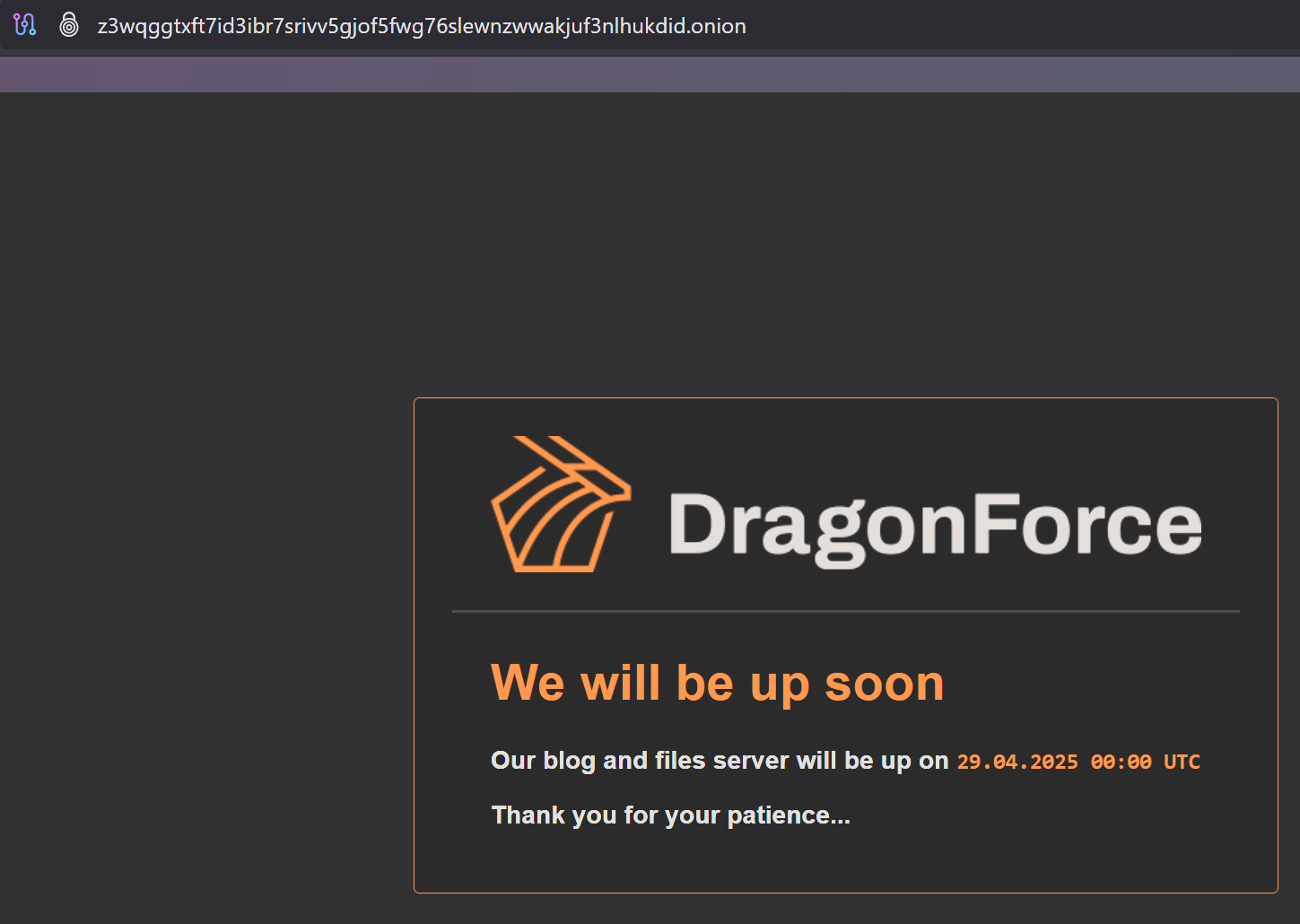
DragonForce's portal is still offline, several days now.
tags: #cybersecurity #threathunting #threatintel #yaraify
Who loves YARAify? We do! 💛 And now there’s even more to love with the latest cool features making 🕵️♂️ threat hunting easier:
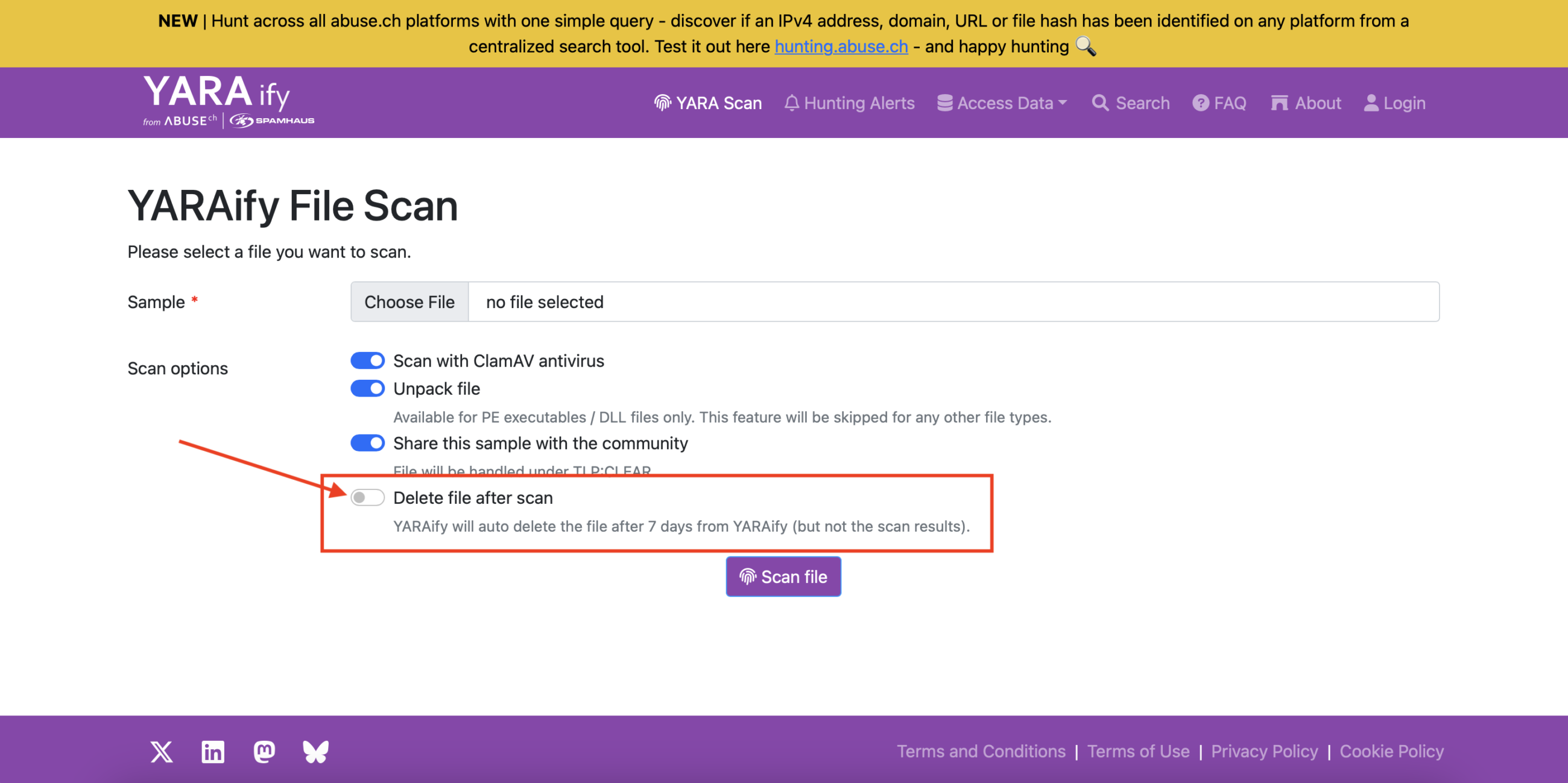
👉 Auto-delete files after scanning! If enabled, YARAify now deletes raw files after 7 days - while keeping scan results and metadata available. Want to keep those juicy files private? You can still disable file sharing ⛔
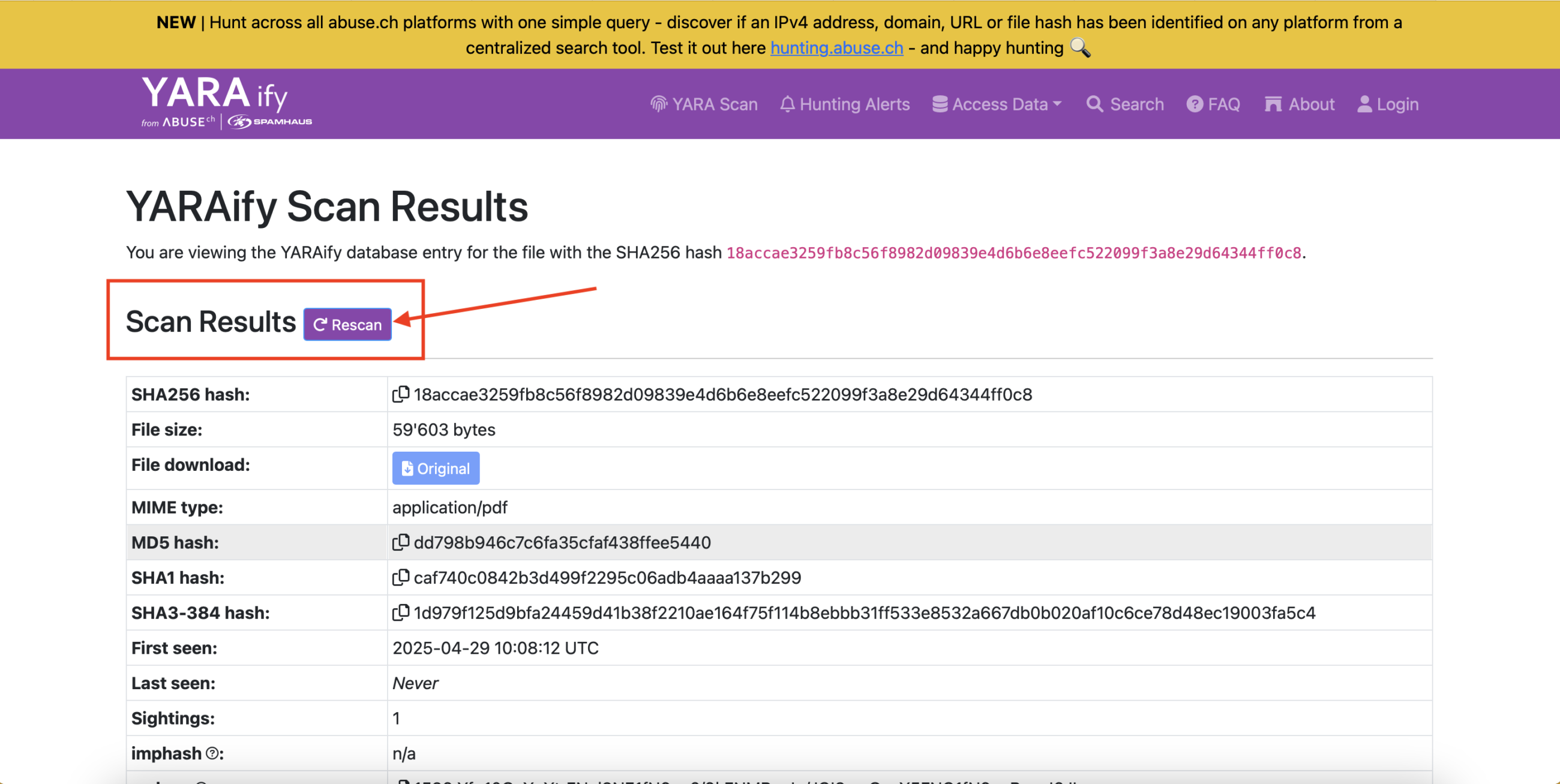
👉 Trigger a file rescan for a previously uploaded sample! Also accessible via the API. ✨ Bonus: Grab Python 3 script from our GitHub repo: https://github.com/abusech/YARAify
👉 Deploy YARA rules directly via the API! ✨ And, yes, there’s a sample script on GitHub for that too!
🎥 Want a walkthrough? Jump to 11:08 in this demo to see these updates in action:
https://www.youtube.com/live/xobmSNfZ-sk
tags: #clickfix #threathunting #threatintel #threatintelligence
FWIW, 100% of #ClickFix attacks I've seen have added some kind of inline comment at the end of the command string like I am not a robot to sell the ruse. Definitely worth a threat hunt on command line history.
Several months after this thread, Conduent have finally filed at 8-K for a cyber incident.
They don’t say it, but it was ransomware. Ransomware group was Safepay. This is their second big ransomware incident.
The Fediverse had the thread first.
https://www.sec.gov/ix?doc=/Archives/edgar/data/1677703/000167770325000067/cndt-20250409.htm
Healthcare provider DaVita Inc have filed an 8-K with the SEC for an ongoing ransomware incident.
https://www.sec.gov/Archives/edgar/data/927066/000119312525079593/d948299d8k.htm
Sensata Technologies Holding plc filed an 8-K with the SEC for a ransomware attack which is remarkably honest, and pretty much the textbook example of how to do it well. https://www.sec.gov/ix?doc=/Archives/edgar/data/1477294/000147729425000047/st-20250406.htm
LFTD Partners Inc. filed an 8K with the SEC for a cyber incident.
They purchased $350k in cryptocurrency.. and immediately had it stolen.
“On April 1, 2025, the Company converted $350,000 of its cash into USD Coin (USDC), a digital stablecoin pegged to the U.S. dollar. Shortly thereafter, the digital wallet containing the USDC was compromised by an unauthorized and unknown third party, resulting in the theft of the full amount.”
https://www.sec.gov/ix?doc=/Archives/edgar/data/1391135/000109690625000425/lsfp-20250401.htm
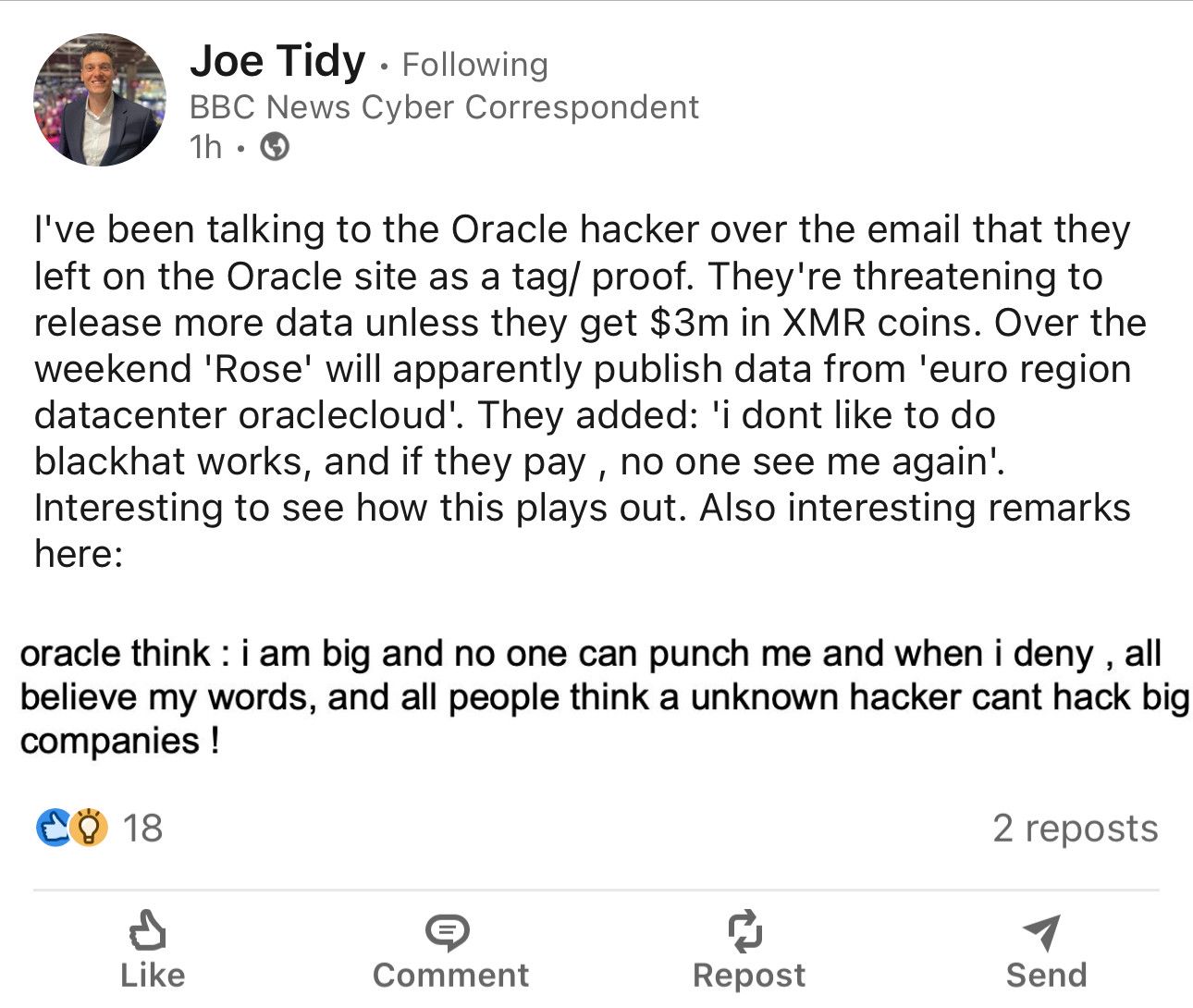
The Oracle cloud threat actor has told the BBC they plan to release European region Oracle Cloud Classic data this weekend.
tags: #azure #credentials #cybersecurity #evilginx #mfa #phishing #sophos #threatintel
(sophos.com) Evilginx: How Attackers Bypass MFA Through Adversary-in-the-Middle Attacks https://news.sophos.com/en-us/2025/03/28/stealing-user-credentials-with-evilginx/
A short descriptive article about Evilginx and how stealing credentials work, a few suggested ways of detecting etc.
Summary:
This article examines Evilginx, a tool that leverages the legitimate nginx web server to conduct Adversary-in-the-Middle (AitM) attacks that can bypass multifactor authentication (MFA). The tool works by proxying web traffic through malicious sites that mimic legitimate services like Microsoft 365, capturing not only usernames and passwords but also session tokens. The article demonstrates how Evilginx operates, showing how attackers can gain full access to a user's account even when protected by MFA. It provides detection methods through Azure/Microsoft 365 logs and suggests both preemptive and reactive mitigations, emphasizing the need to move toward phishing-resistant FIDO2-based authentication methods.
Update: security vendor Resecurity hacked Blacklock and published their shell history, accounts etc.
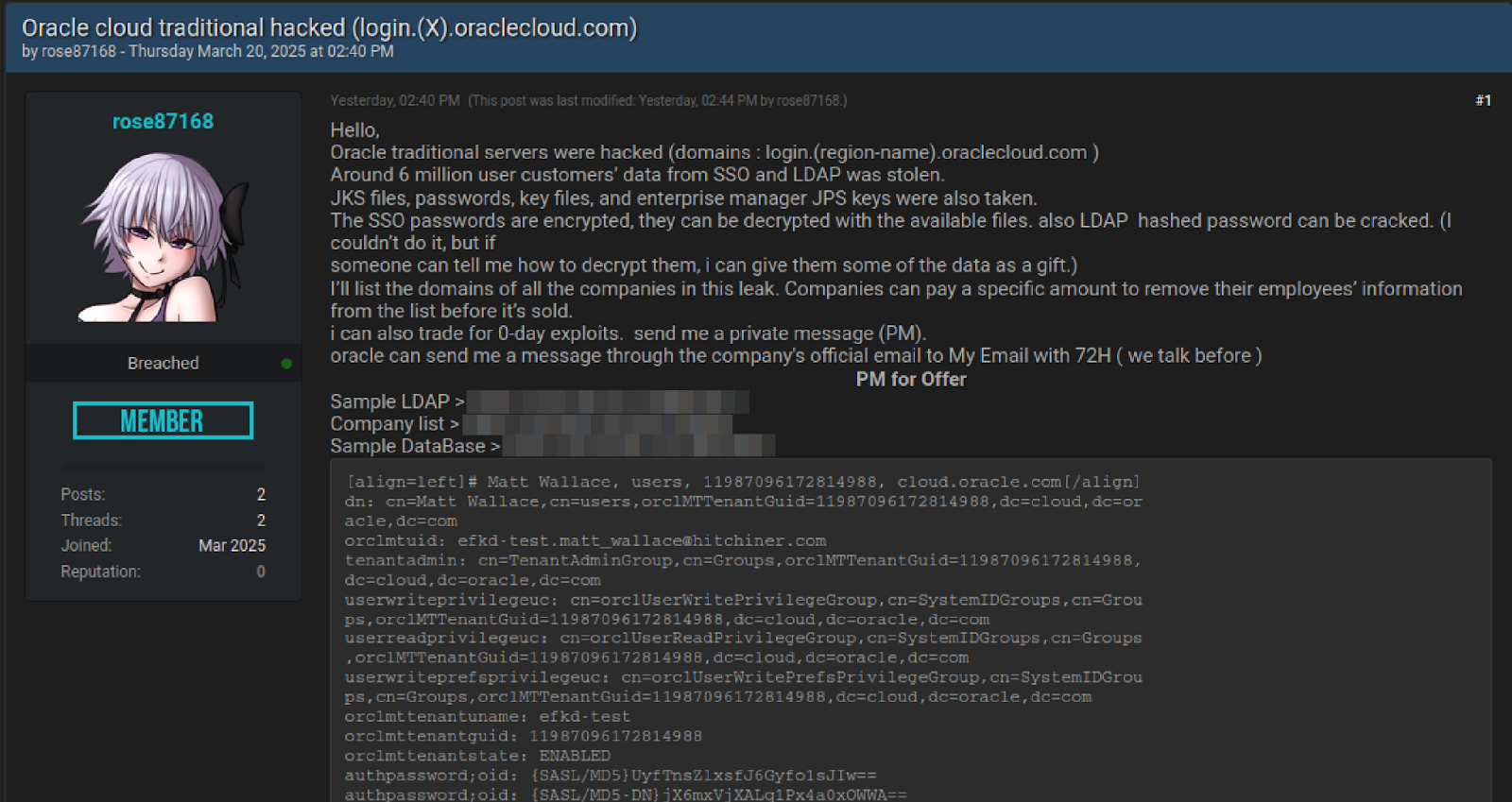
Somebody is claiming to have exfiltrated 6 million lines of data with Oracle Cloud’s SSO and LDAP that includes JKS files, encrypted SSO passwords, key files and enterprise manager JPS keys from servers on login.*.oraclecloud.com
The poster has no prior reputation, it is unclear if they're LARPing. Some of the sample data does align with prior infostealer logs, I'm told. https://breachforums.st/Thread-SELLING-Oracle-cloud-traditional-hacked-login-X-oraclecloud-com
Black Basta ransomware group is indeed dead, post hack and dump of their chats.
Blacklock ransomware group aka El Dorado aka Dragon Force appear to have been hacked. Or should I say free pentest.