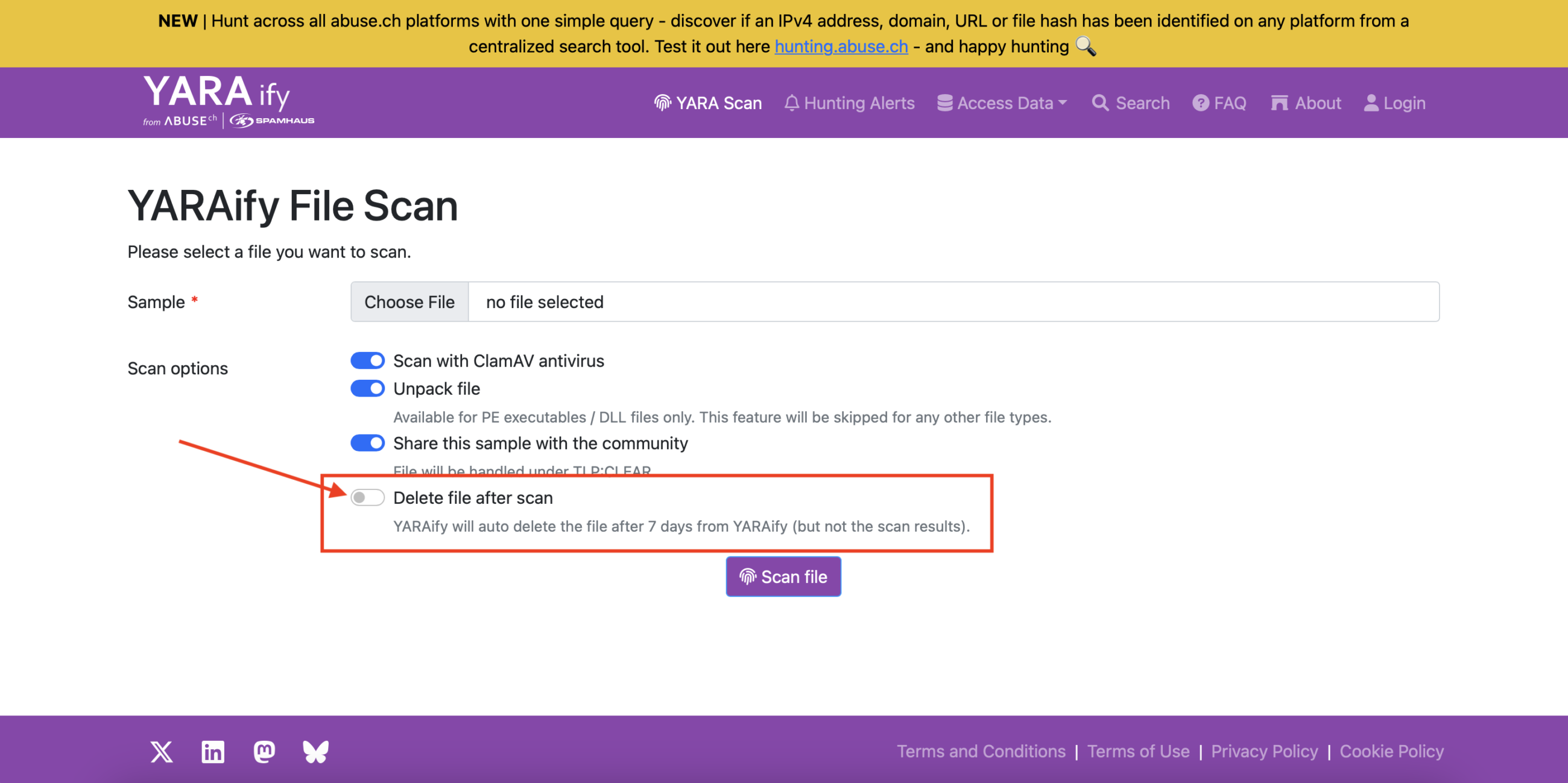
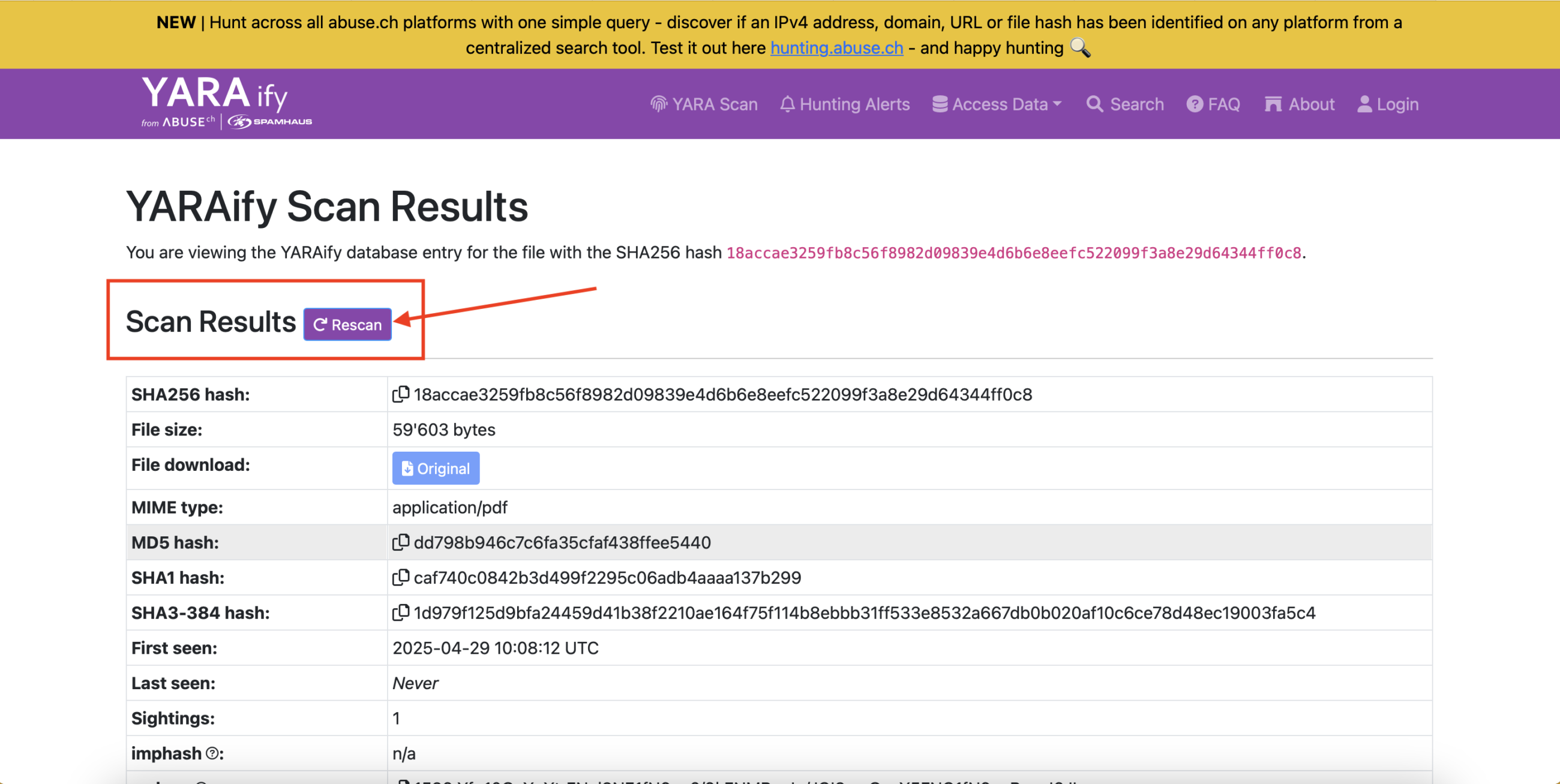
Who loves YARAify? We do! 💛 And now there’s even more to love with the latest cool features making 🕵️♂️ threat hunting easier:
👉 Auto-delete files after scanning! If enabled, YARAify now deletes raw files after 7 days - while keeping scan results and metadata available. Want to keep those juicy files private? You can still disable file sharing ⛔
👉 Trigger a file rescan for a previously uploaded sample! Also accessible via the API. ✨ Bonus: Grab Python 3 script from our GitHub repo: https://github.com/abusech/YARAify
👉 Deploy YARA rules directly via the API! ✨ And, yes, there’s a sample script on GitHub for that too!
🎥 Want a walkthrough? Jump to 11:08 in this demo to see these updates in action:
https://www.youtube.com/live/xobmSNfZ-sk