Write up on the LockBit hack https://www.bleepingcomputer.com/news/security/lockbit-ransomware-gang-hacked-victim-negotiations-exposed/
Somebody has hacked LockBit. I’m going to guess DragonForce. They’ve dumped their victim payment chats and backend SQL.
Masimo, the e-watch maker, has filed an 8-K with the SEC for a ransomware incident.
They don’t say ransomware, but it is.
Their website was down for 5 days, including investor relations, along with all their customer support numbers and online systems. They quietly fixed the website, then filed with the SEC. https://www.sec.gov/ix?doc=/Archives/edgar/data/937556/000110465925045035/tm2514064d1_8k.htm
One of M&S’ biggest suppliers have said they have reverted to pen and paper for orders due to M&S lacking IT.
Additionally, M&S staff are raising concern about how they will be paid due to lack of IT systems.
M&S are over a week into a ransomware incident and still don’t have their online store working.
https://www.bbc.com/news/articles/cvgnyplvdv8o
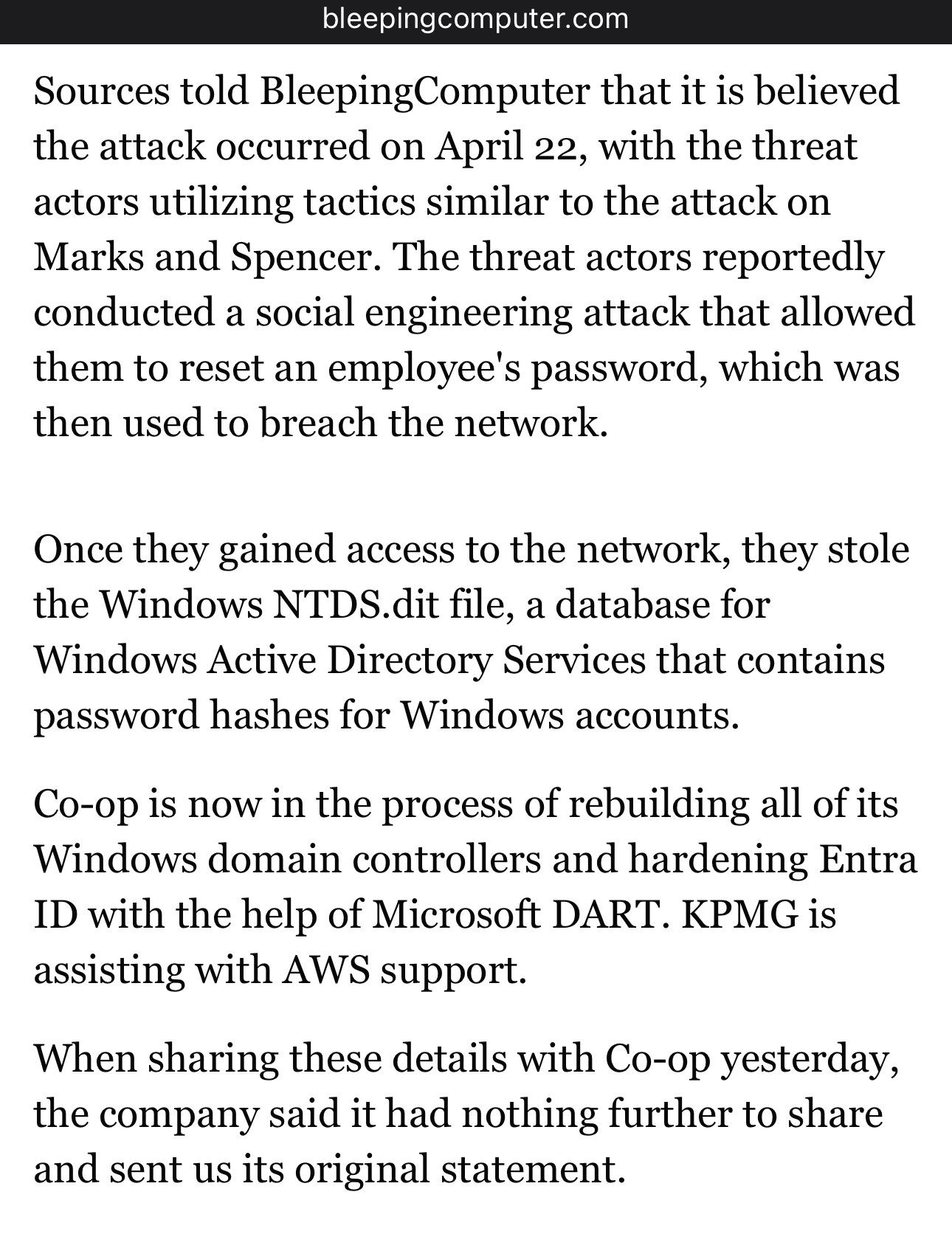
Bleeping Computer have more on the Co-op breach https://www.bleepingcomputer.com/news/security/co-op-confirms-data-theft-after-dragonforce-ransomware-claims-attack/
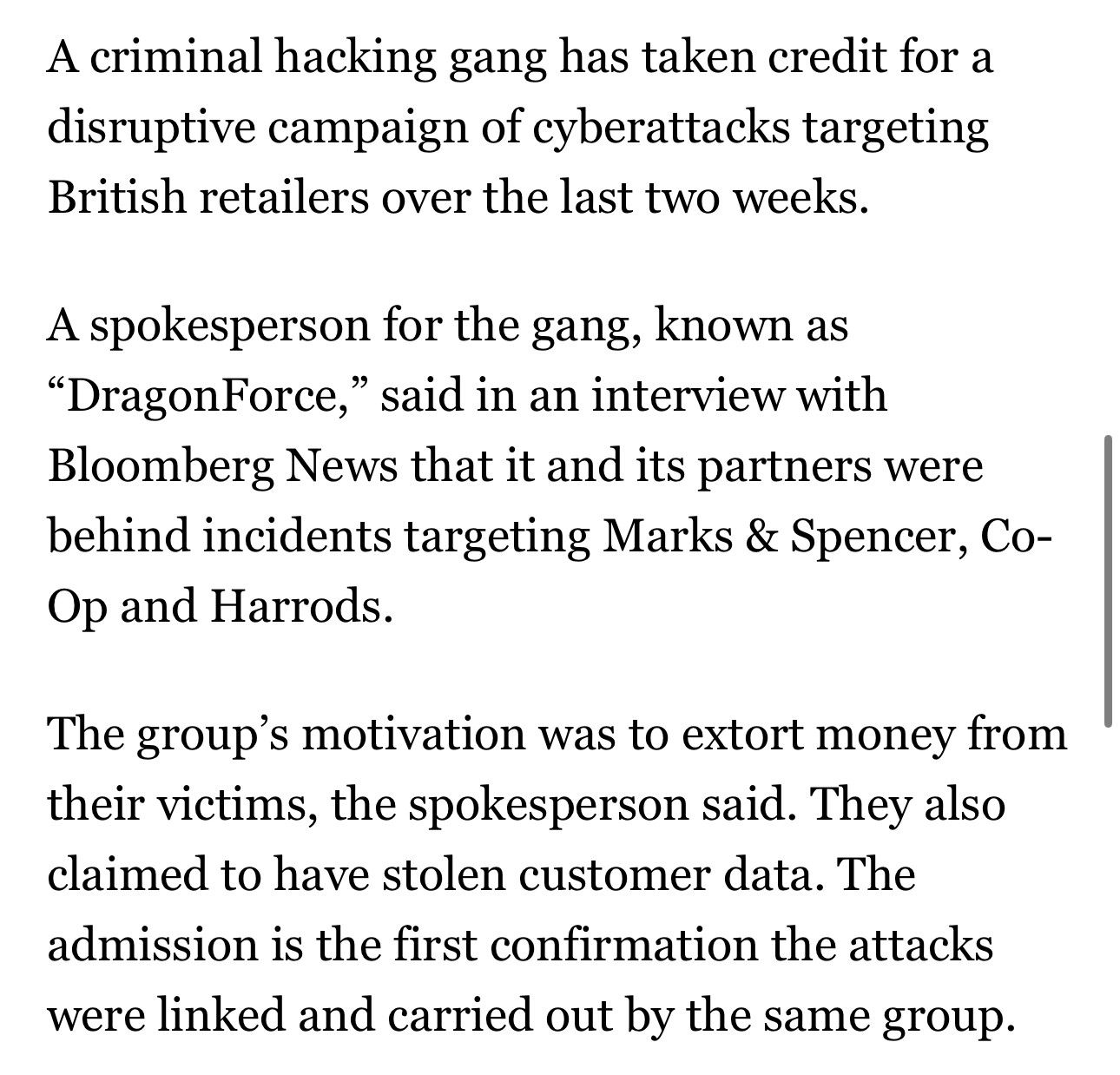
DragonForce Ransomware Cartel are claiming credit for attacks on Marks and Spencer, Co-op and Harrods and say more victim orgs are coming https://www.bloomberg.com/news/articles/2025-05-02/-dragonforce-hacking-gang-takes-credit-for-uk-retail-attacks
DragonForce's portal is still offline, several days now.
Several months after this thread, Conduent have finally filed at 8-K for a cyber incident.
They don’t say it, but it was ransomware. Ransomware group was Safepay. This is their second big ransomware incident.
The Fediverse had the thread first.
https://www.sec.gov/ix?doc=/Archives/edgar/data/1677703/000167770325000067/cndt-20250409.htm
Healthcare provider DaVita Inc have filed an 8-K with the SEC for an ongoing ransomware incident.
https://www.sec.gov/Archives/edgar/data/927066/000119312525079593/d948299d8k.htm
Sensata Technologies Holding plc filed an 8-K with the SEC for a ransomware attack which is remarkably honest, and pretty much the textbook example of how to do it well. https://www.sec.gov/ix?doc=/Archives/edgar/data/1477294/000147729425000047/st-20250406.htm
tags: #freepress #journalism #ransomware
A little ray of sunshine:
The Journal Times, part of Lee Enterprises, had been seriously impacted by the #ransomware attack by Qilin in February. Today, they announced that they are back to full strength: https://journaltimes.com/opinion/column/article_856d2fed-473b-4683-bbf4-61e8fd157830.html
Sincere congrats to them after what was almost two months of intensive and dedicated efforts to fully recover.
tags: #asd #australia #cybersecurity #infosec #ransomware
Dealing with something ridiculous at the moment that is a great example of just how 'easy' it really is to close down exposed data:
Found a server recently with no access controls at all that was hit by ransomware in May 2024 and most of the data is encrypted. (It got hit by an automated script, it wasn't targeted by a ransom group)
Found a non encrypted directory:
The company is STILL uploading, monthly, hundreds of millions of records of logs with their clients data.
Tried to reach out to the company, nothing. Company is from AUS so I tried ASD, nothing.
I sent an email to AUSCERT, they validated with me the issue and forwarded the information and my contact to ASD, they also tried to reach out to the company themselves.
Not a word from anyone and the server is still exposed a month after my initial alerts.
Logs are still being uploaded to the server so it's obvious no one did anything.
So what am I supposed to do here?
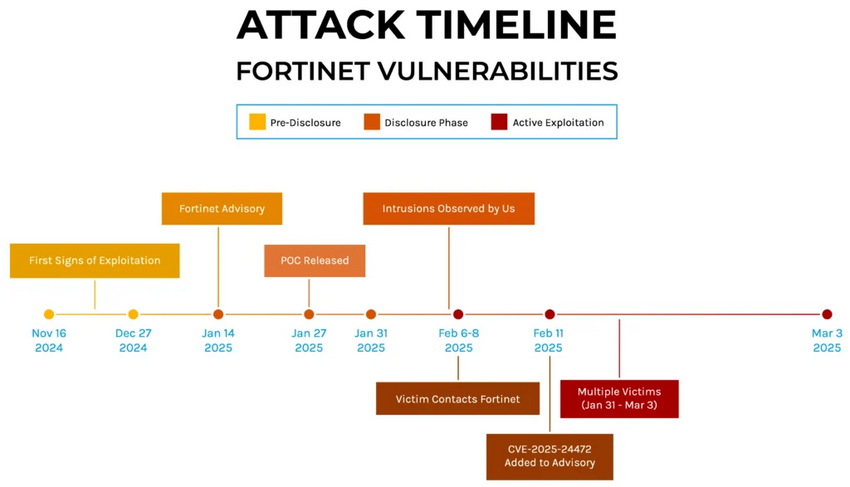
tags: #fortinet #mora_001 #ransomware
to: https://ioc.exchange/users/CERT_at
CERT.at investigates ransomware attacks via critical Fortinet vulnerabilities (FortiOS, FortiProxy) and recommends urgent forensic investigations of all devices that didn't have FortiOS 7.0.16 installed before 2025-01-27, when the PoC for CVE-2024-55591 was published. Those devices may be compromised despite having been patched later.
Check (German) warning by @CERT_at
https://www.cert.at/de/warnungen/2025/3/ransomware-gruppen-nutzen-weiterhin-kritische-fortinet-schwachstellen-warnung-vor-gepatchten-aber-bereits-kompromittierten-geraten
Long story with Forescout:
https://www.forescout.com/blog/new-ransomware-operator-exploits-fortinet-vulnerability-duo/
Black Basta ransomware group is indeed dead, post hack and dump of their chats.
tags: #dataloss #financialtheft #malware #ransomware
New cyber threat research from Proofpoint highlights how attackers are adapting to law enforcement disruptions, leveraging trusted software to evade detection and compromise systems.
This blog details our team's findings: https://www.proofpoint.com/us/blog/threat-insight/remote-monitoring-and-management-rmm-tooling-increasingly-attackers-first-choice?campaign=2025&utm_medium=social_organic.
tags: #BlackBasta #cti #ctiforall #gayint #leak #ransomware #threatintel #threatintelligence
For some reason people are sharing llm garbage instead of the real chat logs for black basta. Here are the real logs and the telegram channel they're being shared in: https://t[.]me/shopotbasta/21
CTI is a team sport. Not a secret boys club. Sharing is caring.
tags: #ransomware #threatintel
to: https://infosec.exchange/users/cR0w
Law enforcement confirm they did a takedown of 8base ransomware group. You heard it here on Mastodon first thanks to @cR0w
https://techcrunch.com/2025/02/10/global-police-operation-seizes-8base-ransomware-gang-leak-site/
tags: #ransomware #threatintel
to: https://infosec.exchange/users/cR0w
8base ransomware group has apparently been seized or done an exit scam.
Two of its Tor portals say "This hidden site and the criminal content have been seized by the Bavarian State Criminal Police Office on behalf of the Office of the Public Prosecutor General in Bamberg"
They had been hitting some high profile targets in recent times.
HT @cR0w
The New York Blood Center was already having a blood shortage emergency and then they got hit with a ransomware attack.
Whoever hit them: please, please, please: you are putting more lives at risk every day. Give them a decryptor.
ENGlobal Corporation has filed an updated 8K with the SEC to say they have evicted the ransomware actor from their network and restored service, two months later.
https://www.sec.gov/ix?doc=/Archives/edgar/data/933738/000165495425000798/eng_8ka.htm
Cl0p have started publishing the stolen Cleo MFT data. Have confirmed with one of the victim orgs it came from their Cleo server.
I didn't realize #cl0p started posting their latest victims. Everything else listed is supposedly getting published Friday 24 January.
tags: #aws #cloudforensics #codefinger #for509 #ransomware
#Ransomware threat actors are increasingly abusing AWS's Server-Side Encryption (SSE-C) to encrypt S3 buckets without needing to drop malware. Most recently a TA known as #Codefinger is using this technique.
🕵 Make sure you're monitoring S3 and encryption activity via CloudTrail & GuardDuty.
https://www.halcyon.ai/blog/abusing-aws-native-services-ransomware-encrypting-s3-buckets-with-sse-c
Space Bears changed their ATOS page to say "SOLD", which feels like it's not true given they never provided proof.
With prior victims they provided download links which had legit data, so they've damaged their reputation over this one.
The Brain Cipher #ransomware gang has begun to leak documents stolen in an attack on Rhode Island's "RIBridges" social services platform☝️☠️ #cybercrime