Here is a traffic distribution system (TDS) in action. Fairly often when talking about TDS, I get the rebuttal: when i visited that domain, i only saw parking. Exactly. That's the point. :) A malicious TDS is like a router for malware -- the goal is to bring the best victims to the best malicious offering. And to play dead when it looks like they might be caught, aka look like parking or search ads.
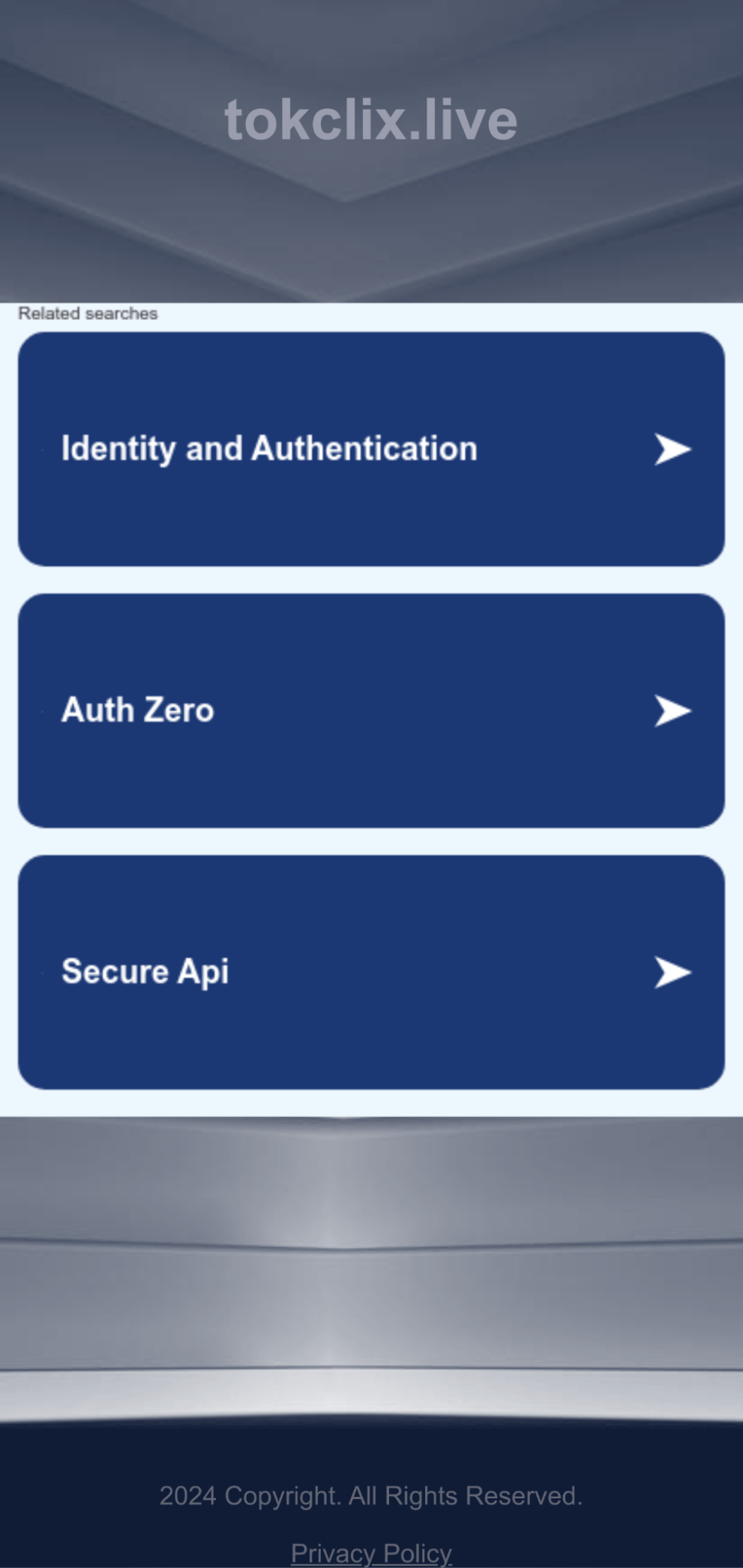
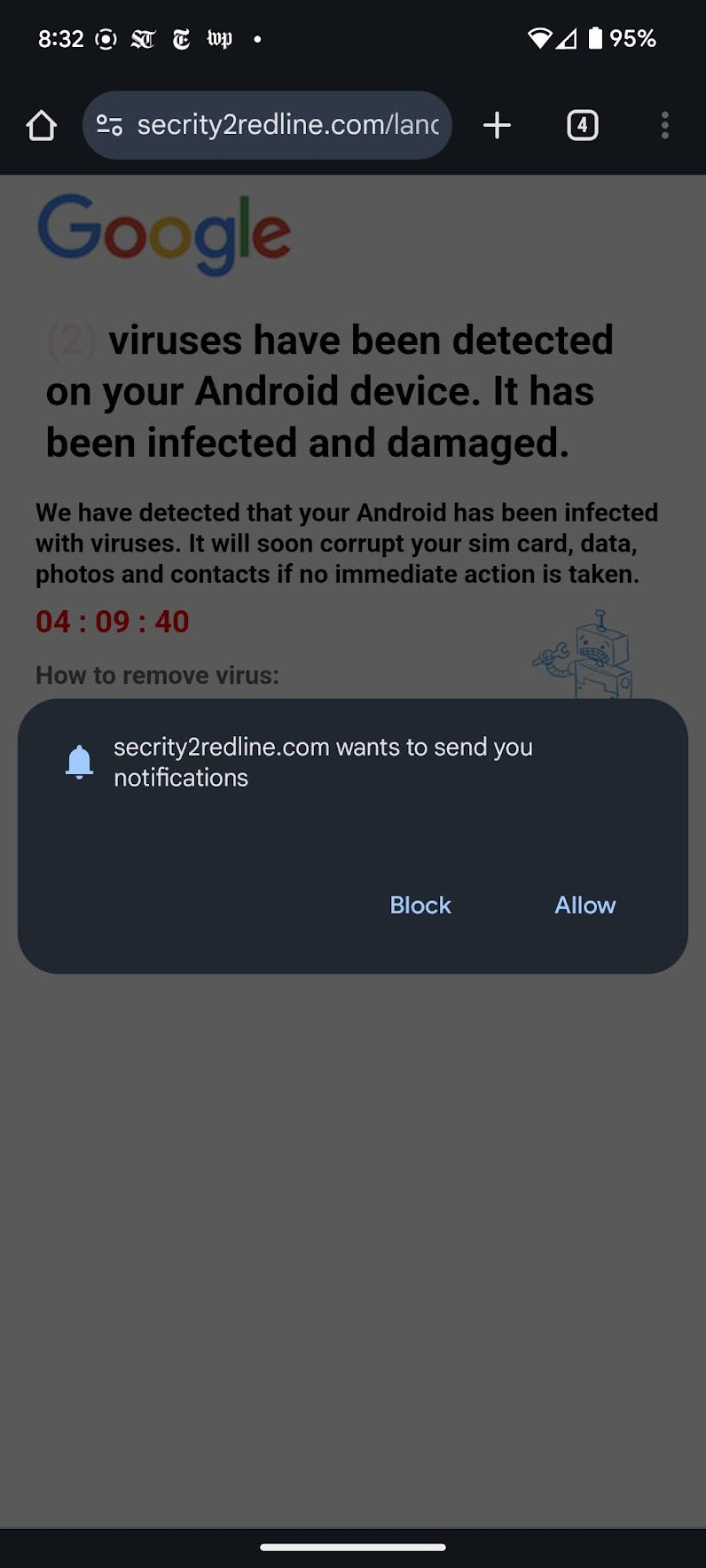
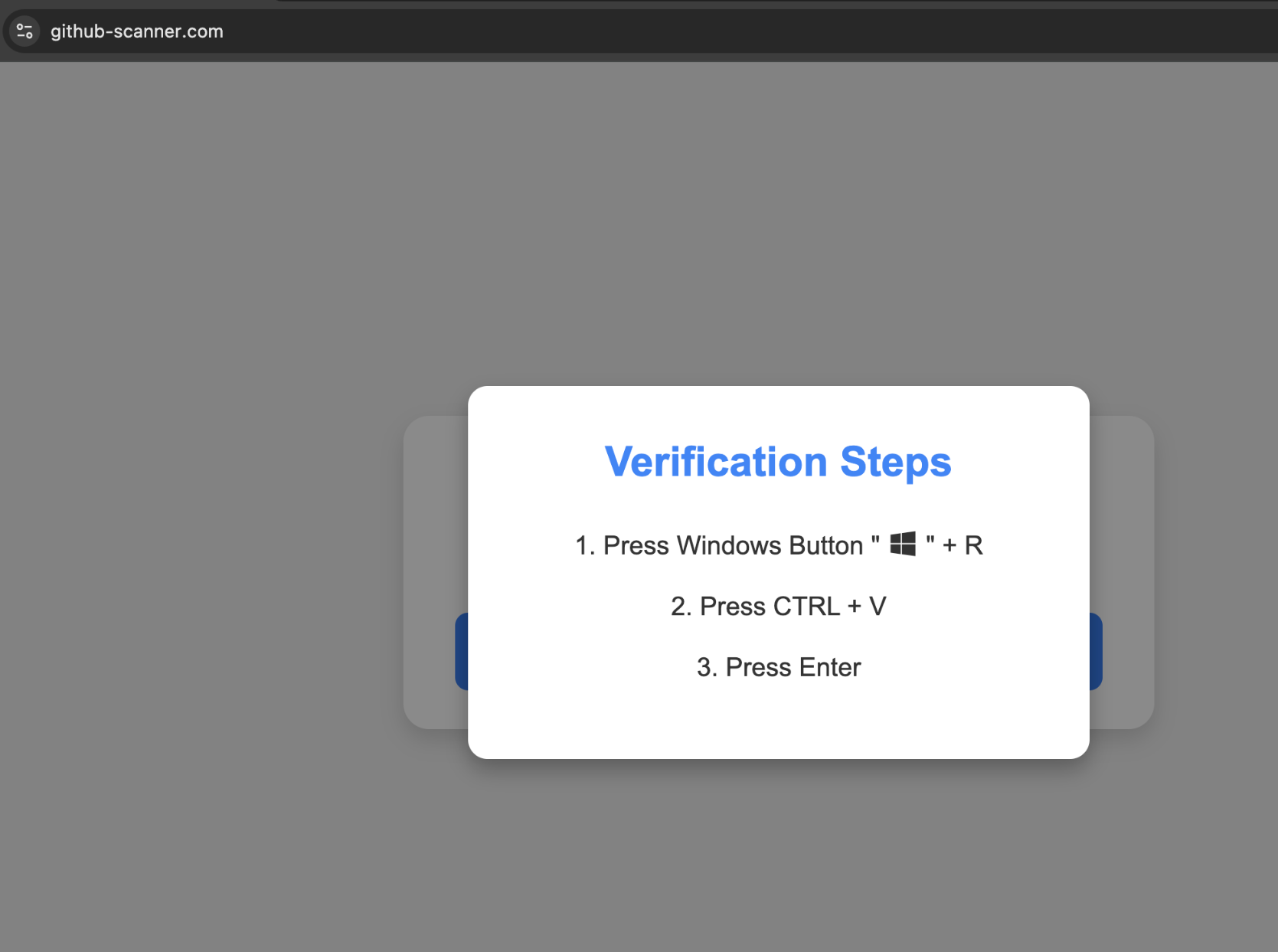
What these images show is the difference between visiting the site tokclix[.]live from a scanner (urlscan) versus from a real Android phone. The former leads you to (sketchy) search arbitrage and the latter is classic scareware. This is what a TDS does.
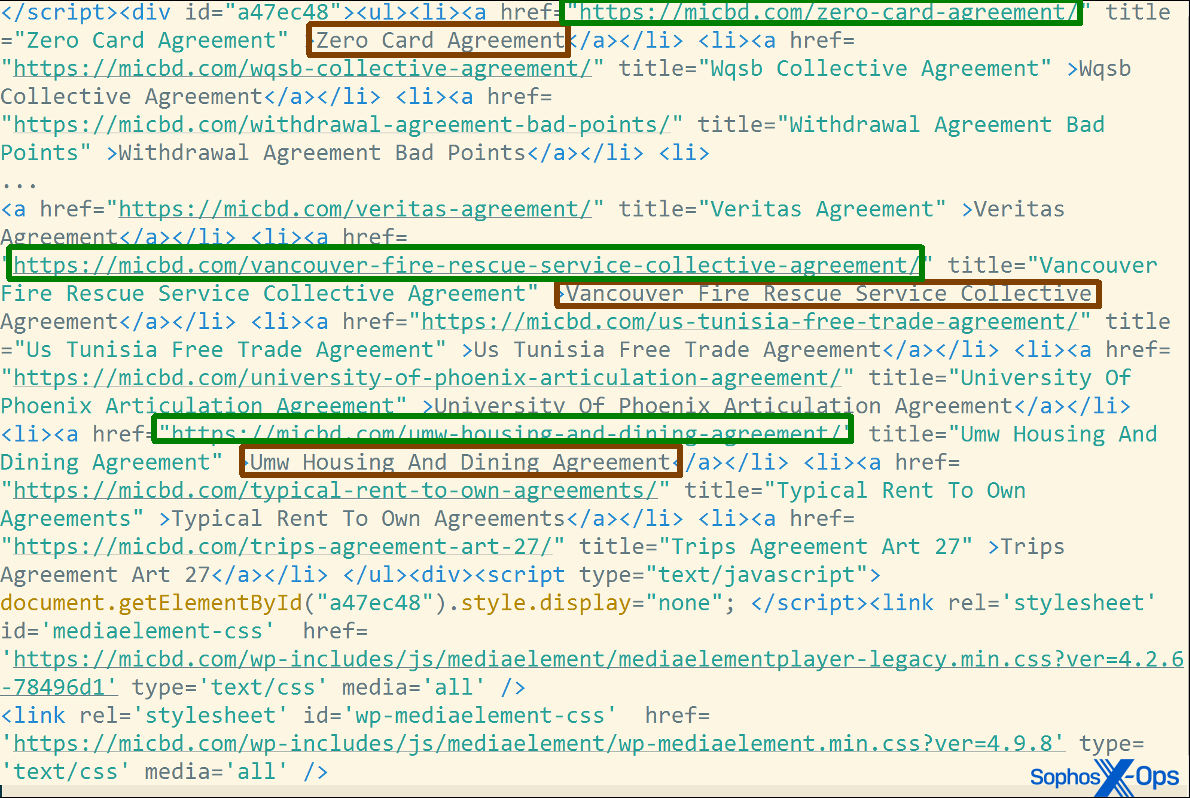
Found this particular one while researching search arbitrage so it is fairly random. started with an old post on BlackHat World but the domains were all still live. On the screen capture you can see the redirects through the TDS.
The imgur video shows the original click to scareware -- watch the redirects.
#InfobloxThreatIntel #tds #dns #malware #threatintel #cybercrime #cybersecurity #infosec #scam #phishing