In the course of its investigations, @volexity frequently encounters malware samples written in Golang. This reflects the increase in popularity of the Golang generally, and presents challenges to reverse engineering tools.
Today, @volexity is releasing GoResolver, open-source tooling to help reverse engineers understand obfuscated samples. @r00tbsd & Killian Raimbaud presented details at INCYBER Forum earlier today.
GoResolver uses control-flow graph similarity to identify library code in obfuscated code, leaving analysts with only malware functions to analyze. This saves time & speeds up investigations!
Check out the blog post on how GoResolver works and where to download it: https://www.volexity.com/blog/2025/04/01/goresolver-using-control-flow-graph-similarity-to-deobfuscate-golang-binaries-automatically/
tags: #dfir #malwareanalysis #reversing
to: https://infosec.exchange/users/r00tbsd https://infosec.exchange/users/volexity
tags: #blueteam #cobaltstrike #forensics #malwareanalysis
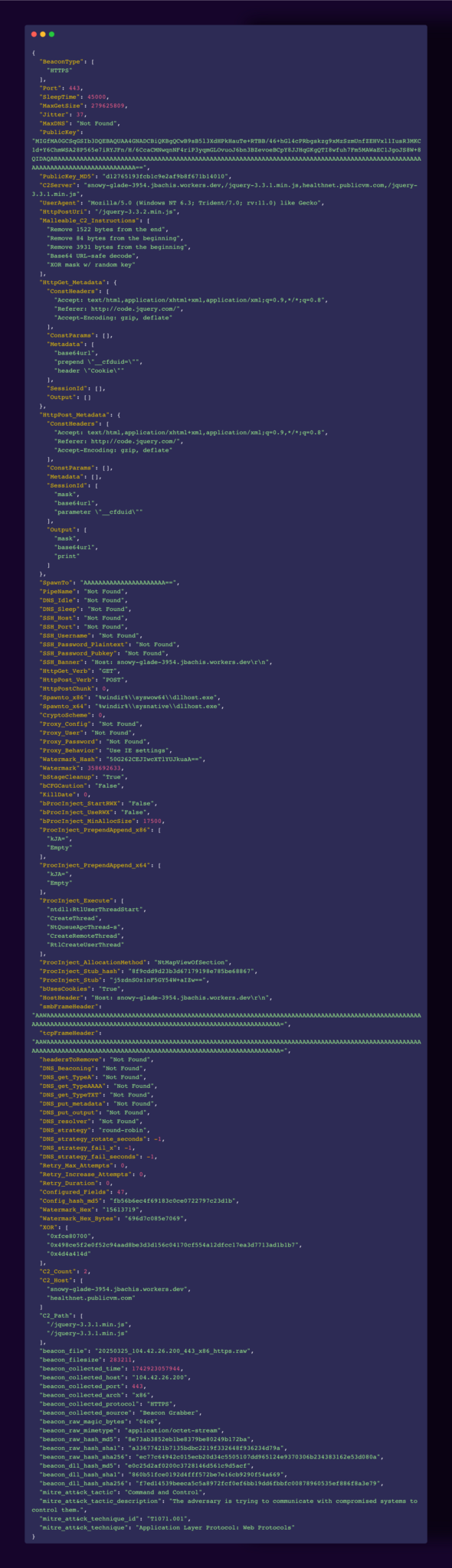
For hobbyist Cobalt Strike Beacon collectors, note that the recently announced 4.11 update introduces a number of changes to frustrate Beacon configuration extraction, namely through the new `transform-obfuscate` field.
When set, this field can apply multiple layers of encoding, encryption and compression (with some recent Beacons observed with a 32 byte XOR key, configurable upto 2048 bytes!).
While still reasonably trivial to decode manually, standard automated workflows (say, through the SentinelOne parser) will now fail, not least because of changes to the well-known field markers.
Beacons with these characteristics have thus far been observed with watermarks indicative of licensed instances, though I imagine it is only a matter of time before the 4.11 capabilities become accessible to all manner of miscreants.
A sample configuration, via a staged Beacon on 104.42.26[.]200 is attached, including the three distinct XOR keys used to decode it.
https://www.cobaltstrike.com/blog/cobalt-strike-411-shh-beacon-is-sleeping
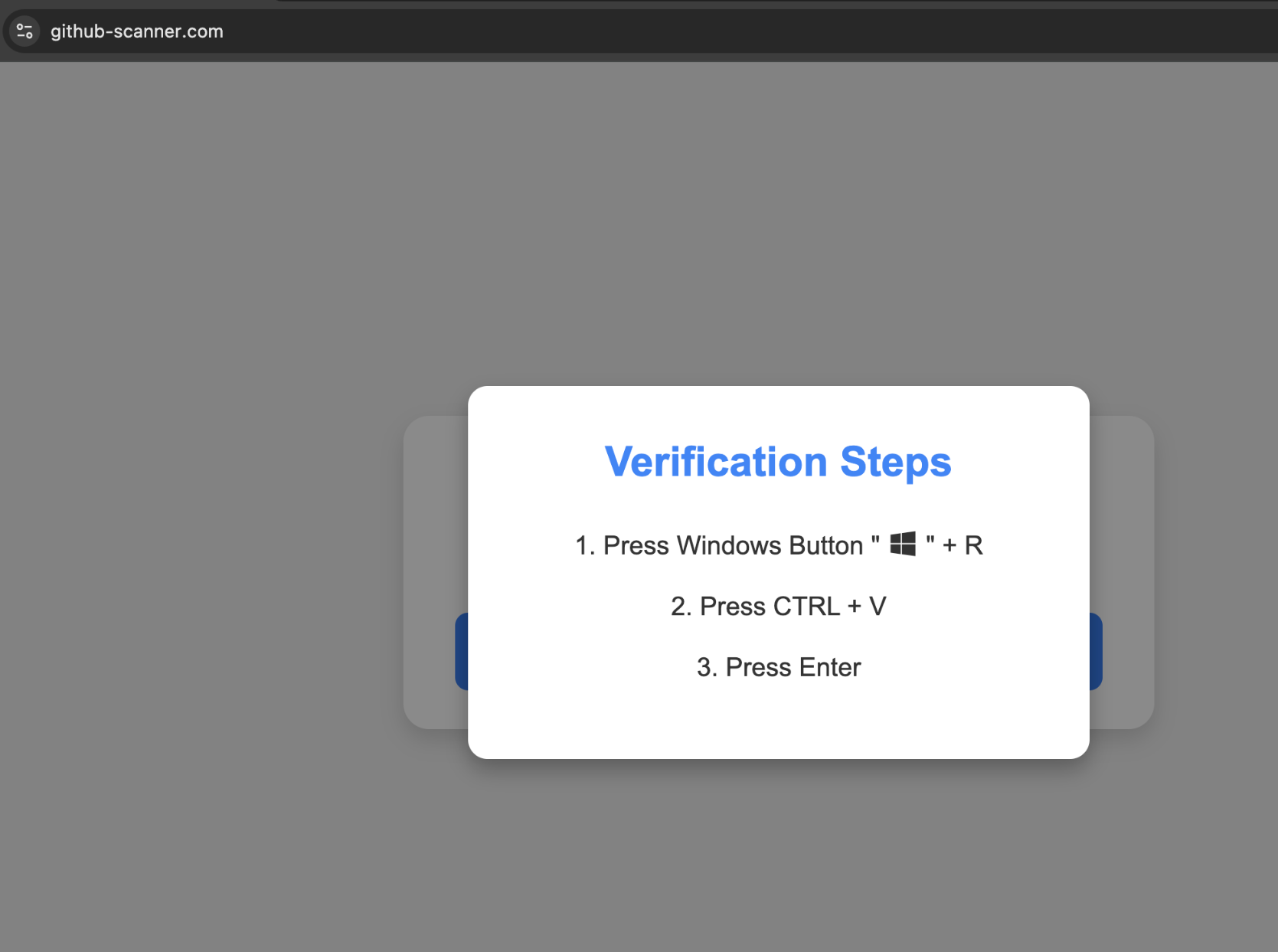
A funny phishing targeting GitHub users with an email notification about a security issue on a existing repository.
Then the captcha verification on a malicious website is trying to trick the user to run a shell command on Windows.
🔗 Powershell to be executed by the user
https://gist.github.com/adulau/6cf6f3e9c5bbd9106af8814d0a22f473
🔗 File downloaded https://pandora.circl.lu/analysis/21e8f693-361b-4a04-853c-276f9dd841e4/seed-1XqUr4mADaFYlLAyrBH8oQUBgOoEbceZ586b8h05YyA - Lumma Stealer
🔗 Malicious domain analysis. https://lookyloo.circl.lu/tree/91106035-dfec-4acc-af06-c9fc36c62774