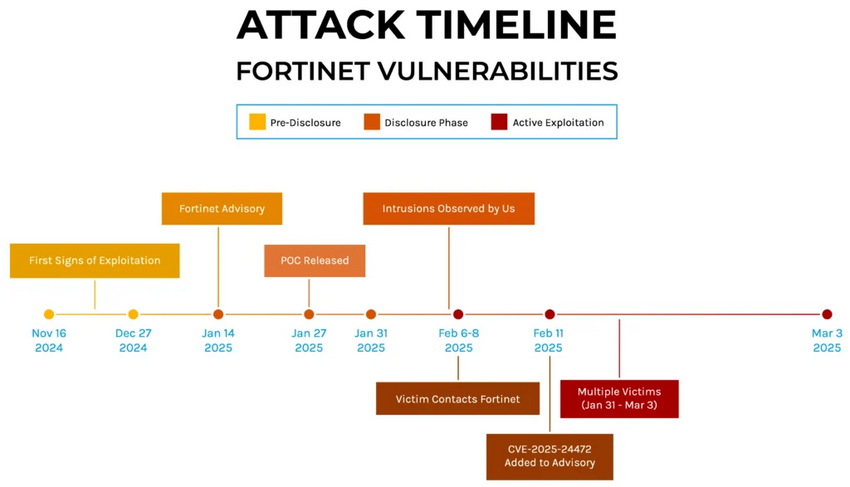
CERT.at investigates ransomware attacks via critical Fortinet vulnerabilities (FortiOS, FortiProxy) and recommends urgent forensic investigations of all devices that didn't have FortiOS 7.0.16 installed before 2025-01-27, when the PoC for CVE-2024-55591 was published. Those devices may be compromised despite having been patched later.
Check (German) warning by @CERT_at
https://www.cert.at/de/warnungen/2025/3/ransomware-gruppen-nutzen-weiterhin-kritische-fortinet-schwachstellen-warnung-vor-gepatchten-aber-bereits-kompromittierten-geraten
Long story with Forescout:
https://www.forescout.com/blog/new-ransomware-operator-exploits-fortinet-vulnerability-duo/