Cl0p have started publishing the stolen Cleo MFT data. Have confirmed with one of the victim orgs it came from their Cleo server.
https://attackerkb.com/topics/geR0H8dgrE/cve-2024-55956/rapid7-analysis
tags: #cleo
to: https://bird.makeup/users/stephenfewer
Full Rapid7 analysis of #Cleo CVE-2024-55956 now available c/o @stephenfewer. It's neither a patch bypass of CVE-2024-50623 nor part of a chain after all — totally new bug, different exploitation strategies across the two issues (though the same endpoint gets used either way).
I'm not sure it's been mentioned much yet that Cleo evidently released IOCs related to CVE-2024-50623 in October 2024, implying the older bug's been exploited for a minute. Would sure be helpful to know more about who was doing that exploiting, particularly now that Cl0p has claimed credit for last week's attack.
CISA have added the new CVE for the Cleo zero day to KEV.
https://mastodon.social/@cisakevtracker/113647291426972278
CVE ID: CVE-2024-50623
Vendor: Cleo
Product: Multiple Products
Date Added: 2024-12-13
Vulnerability: Cleo Multiple Products Unrestricted File Upload Vulnerability
Notes: https://support.cleo.com/hc/en-us/articles/28408134019735-Cleo-Product-Security-Update ; https://nvd.nist.gov/vuln/detail/CVE-2024-50623
CVE URL: https://nvd.nist.gov/vuln/detail/CVE-2024-50623
Had the threat actor gone more slowly and hit orgs prone to cover ups (ie large enterprises) that would have been a very different outcome.
The smaller Managed Detection and Response vendors have the window to do something very funny and talk about things rather than doing a CrowdStrike, MS etc and doing a cover up - it breaks the race to the bottom, and is one area where the market is getting healthier.
I think the Cleo thing shows the industry and community working very well, btw.
From zero day in an MFT product to approx 2/3rd of servers now offline or patched in days. As far as I know, since mass exploitation began (important caveat) none of the victims had follow on activity, ie ransomware.
That’s a really good outcome. The reason, I think, is openness and transparency - Huntress went public early and everybody leaped on it loudly in the community. Be more open.
Another write up on the Cleo zero day: https://arcticwolf.com/resources/blog/cleopatras-shadow-a-mass-exploitation-campaign/
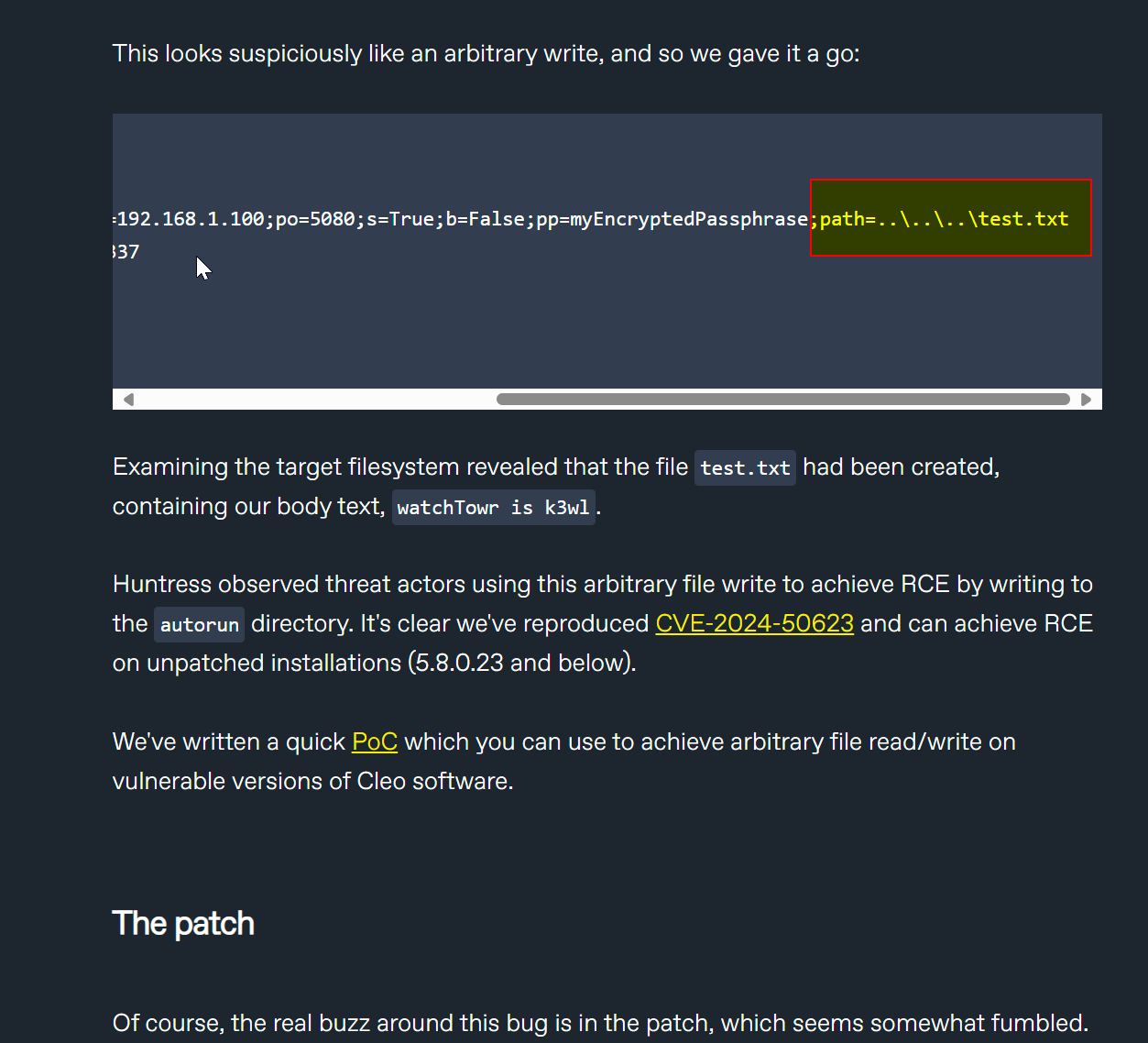
A writeup on the Cleo vulnerabilities, which are under mass exploitation now. Write any file into any folder by using path=..\..\..\ - since it's a webapp, just drop a webshell.
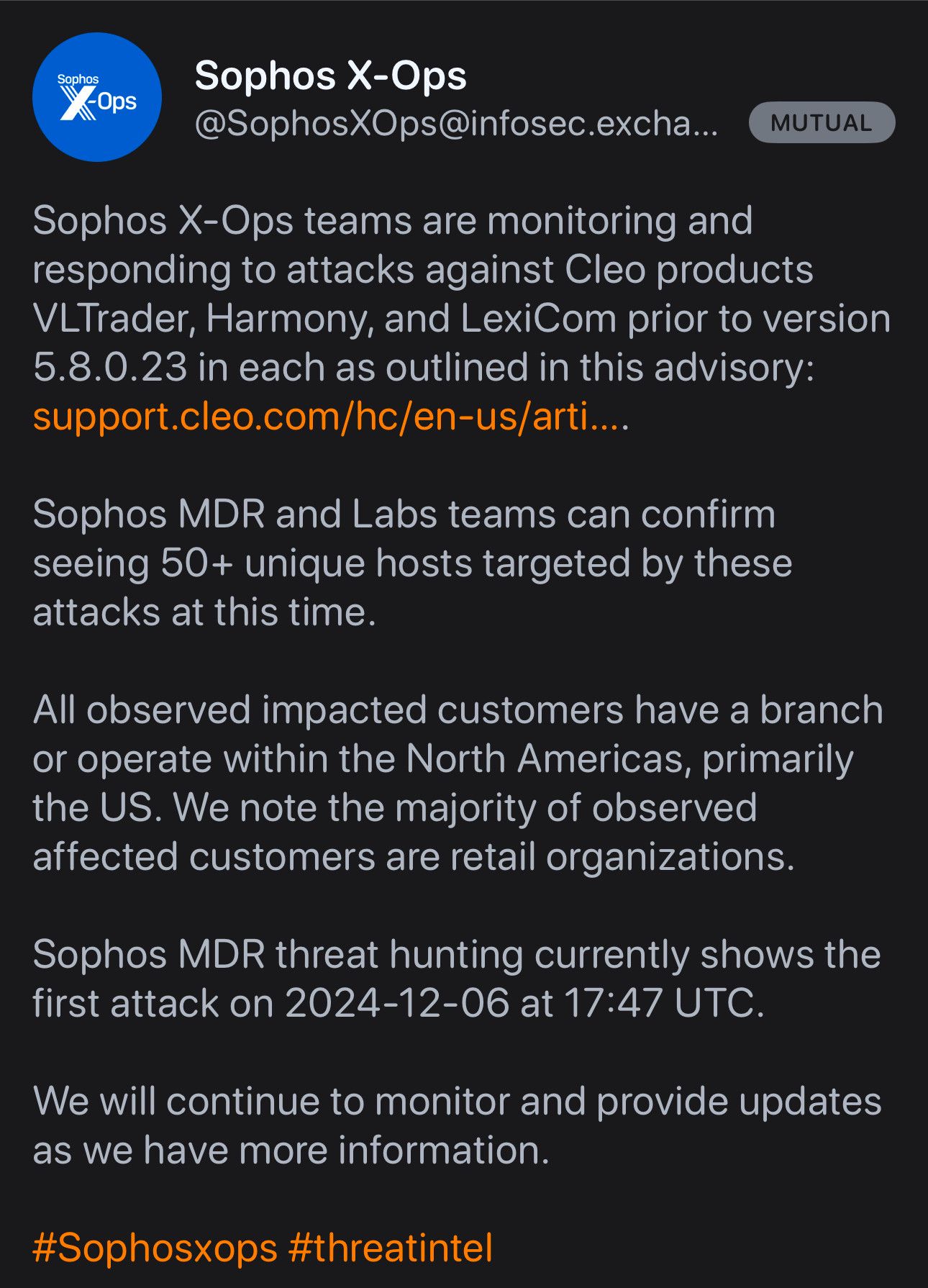
Sophos says they have seen 50+ systems with Cleo enterprise file transfer product zero day exploitation. Huntress say 28+ customers so far. Rapid7 haven’t given numbers.
https://infosec.exchange/@SophosXOps/113631363563332166
Sophos X-Ops teams are monitoring and responding to attacks against Cleo products VLTrader, Harmony, and LexiCom prior to version 5.8.0.23 in each as outlined in this advisory: https://support.cleo.com/hc/en-us/articles/28408134019735-Cleo-Product-Security-Advisory-CVE-Pending.
Sophos MDR and Labs teams can confirm seeing 50+ unique hosts targeted by these attacks at this time.
All observed impacted customers have a branch or operate within the North Americas, primarily the US. We note the majority of observed affected customers are retail organizations.
Sophos MDR threat hunting currently shows the first attack on 2024-12-06 at 17:47 UTC.
We will continue to monitor and provide updates as we have more information.
"In an emailed statement given to TechCrunch, Jorge Rodriguez, SVP of product Development at Cleo, said that a patch for the critical vulnerability is “under development.”
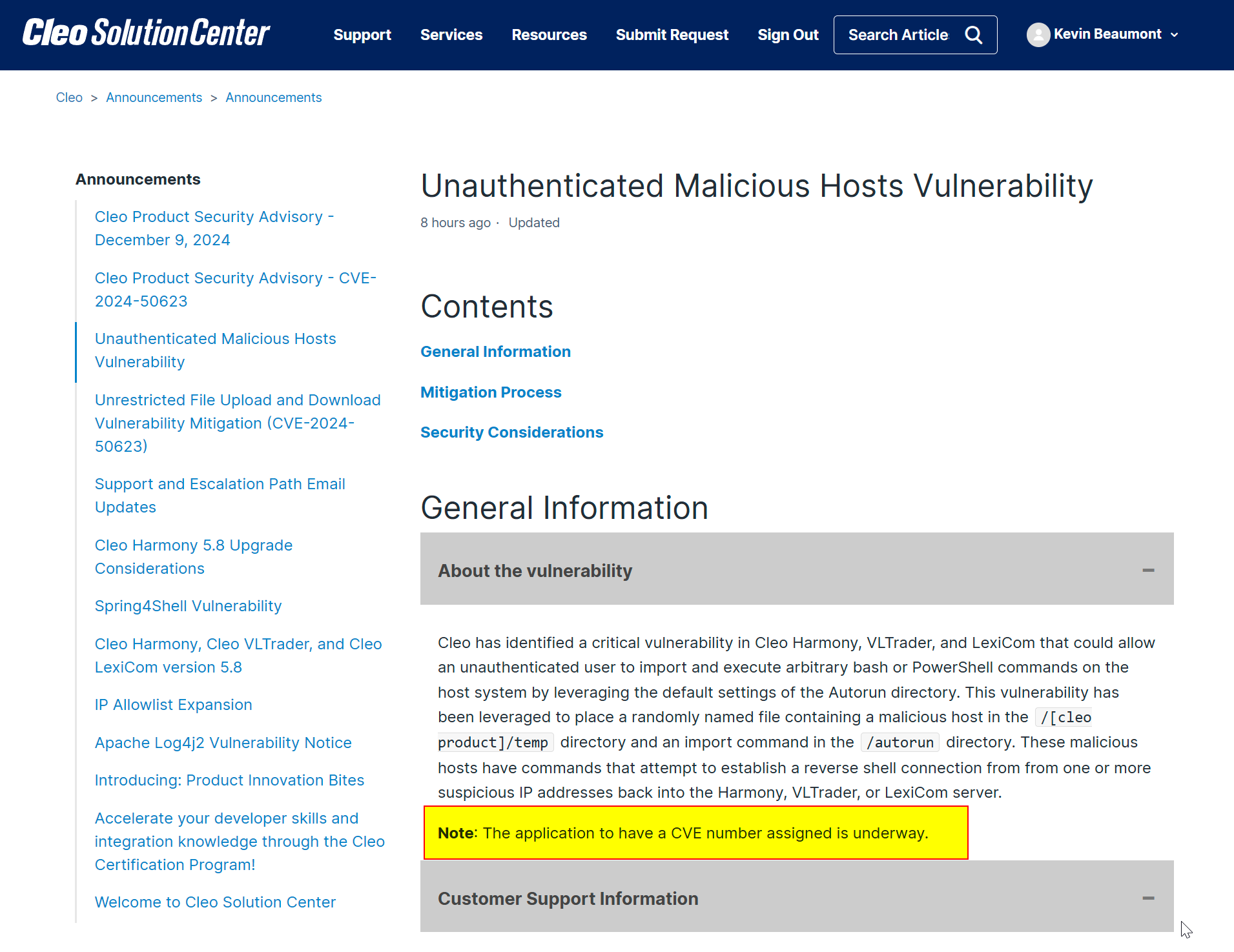
After my toot Cleo have issued a public advisory, they're saying versions up to 5.8.0.23 (not out yet) are impacted.
In terms of threat intel, the ransomware operators I know of only have an exploit for the Windows versions, not Linux.
https://support.cleo.com/hc/en-us/articles/28408134019735-Cleo-Product-Security-Advisory-CVE-Peding
Rapid7 say "As of December 10, Rapid7 MDR has confirmed successful exploitation of this issue in customer environments; similar to Huntress, our team has observed enumeration and post-exploitation activity and is investigating multiple incidents." https://www.rapid7.com/blog/post/2024/12/10/etr-widespread-exploitation-of-cleo-file-transfer-software-cve-2024-50623/
Cleo have issued a (paywalled) advisory about the zero day, saying a new CVE number is being allocated.
i would fully pull the plug on impacted Cleo products until there's vendor clarity btw
Shodan dork (not exhaustive) - the Windows ones are a particular problem in terms of ransomware.
https://beta.shodan.io/search?query=http.html_hash%3A1534766930
This is a build upon Huntress' (excellent) blog https://www.huntress.com/blog/threat-advisory-oh-no-cleo-cleo-software-actively-being-exploited-in-the-wild