NBC News: Hyundai announce recall of more than 42,000 vehicles due to wiring issue that can cause them to roll
I'm posting this again to my main timeline, because it's really frustrating (emphasis mine):
"Beaumont says *admin access to the system isn’t required* to read another user’s Recall database. *Another user with an admin account* can easily grab any other user’s Recall database and all the Recall screenshots by clicking through a simple UAC prompt."
https://arstechnica.com/ai/2024/06/windows-recall-demands-an-extraordinary-level-of-trust-that-microsoft-hasnt-earned/2/
How is this not a contradiction? All demos I've seen clearly show that UAC elevation (from an admin account) is needed to access the DB.
I find the idea of #Recall as baffling as anyone, but as professionals we must clearly communicate the risks, so that *real* threats (e.g. abusive spouse with local admin access) are highlighted and MS can't dismiss them as FUD.
tags: #recall
to: https://infosec.exchange/users/gossithedog https://infosec.exchange/users/tiraniddo
'It’s not a security vulnerability that users can access files that they have access to, even if the file is a little hard to find' by Raymond Chen seems relevant to the #Recall discussion:
https://devblogs.microsoft.com/oldnewthing/20200113-00/?p=103322
Indeed, you can even find @tiraniddo in the comments, who wrote about the topic recently:
https://www.tiraniddo.dev/2024/06/working-your-way-around-acl.html
I still don't see how *cross-user* access might be achieved *without admin* (as reported by @gossithedog ).
tags: #ai #copilot #grouppolicy #recall #windows
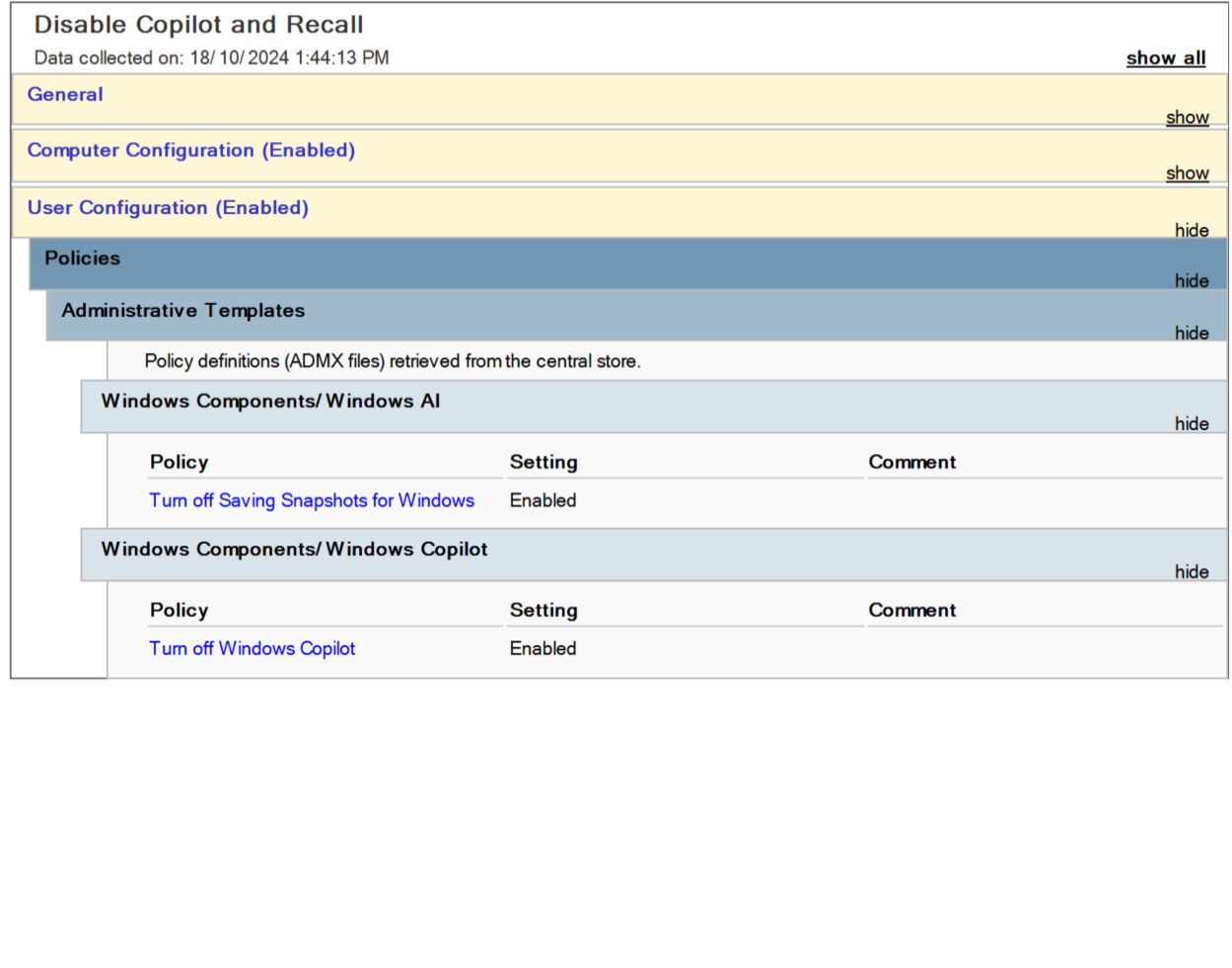
Disabling #Windows #AI features organization-wide using #GroupPolicy.
This will turn off #Recall (the periodic screenshot service) and #Copilot (the AI assistant service). You can do this pre-emptively even before any machines on your domain are running Windows 11 24H2.
1. Download and install the Windows 11 24H2 administrative template files: https://www.microsoft.com/en-us/download/details.aspx?id=106254
2. Add the files from C:\Program Files (x86)\Microsoft Group Policy\Windows 11 Sep 2024 Update (24H2)\PolicyDefinitions to C:\Windows\SYSVOL\domain\Policies\PolicyDefinitions on the domain controller.
3. Start Group Policy Management on the domain controller.
4. Create a group policy object with these values:
User Configuration > Policies > Administrative Templates > Windows Components > Windows AI > Turn off Saving Snapshots for Windows = enabled
User Configuration > Policies > Administrative Templates > Windows Components > Windows Copilot > Turn off Windows Copilot = enabled
5. Link the group policy object in at an appropriate level in your domain.