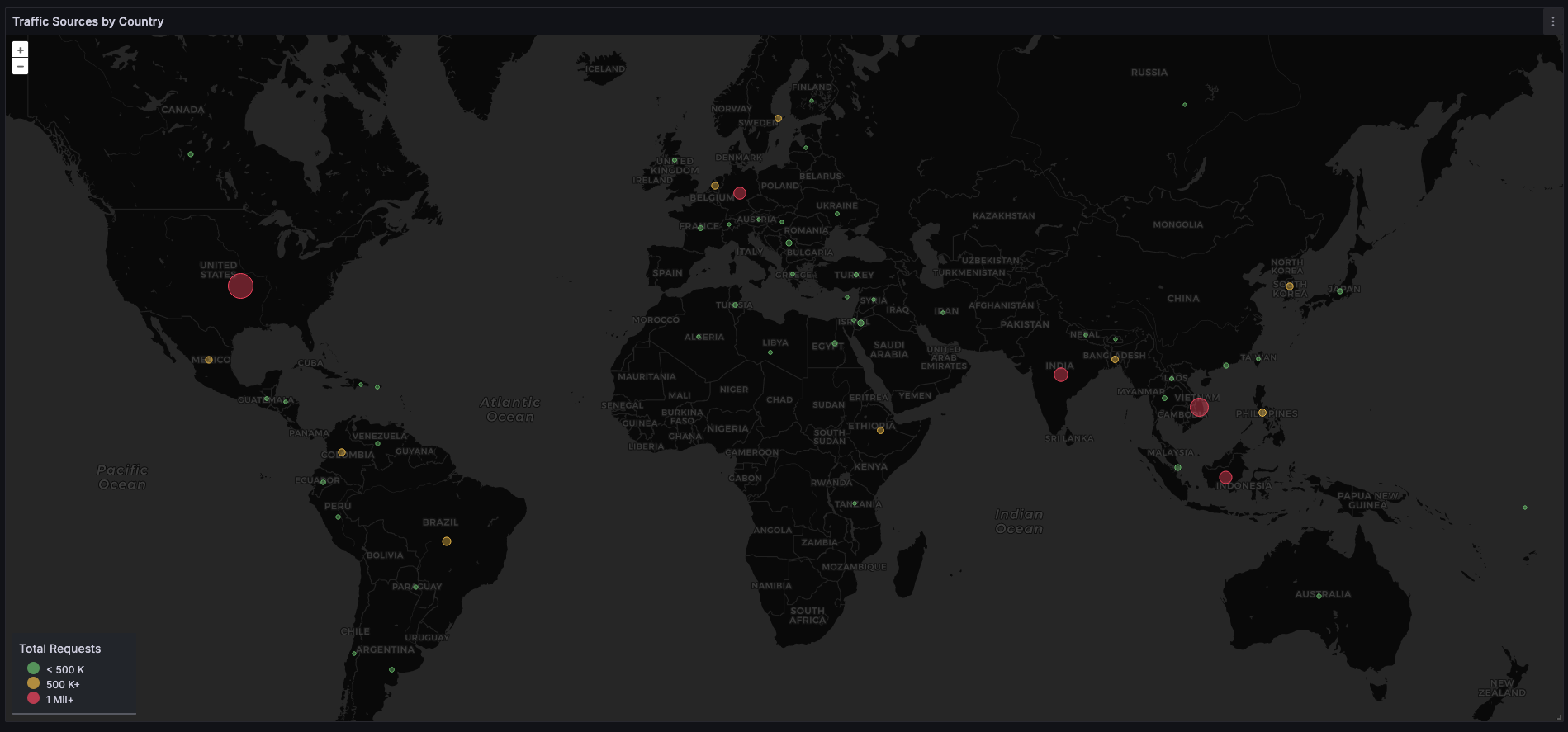
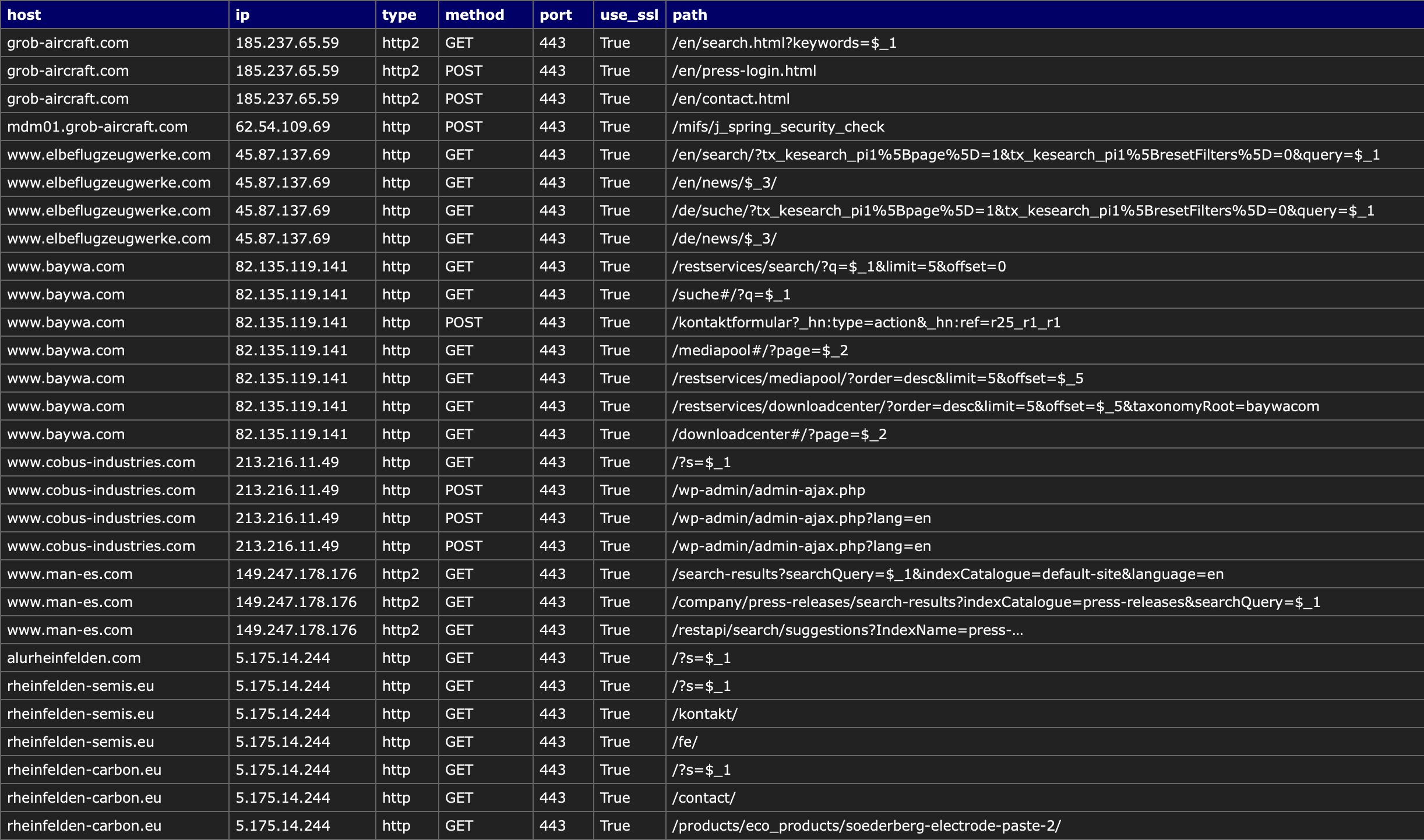
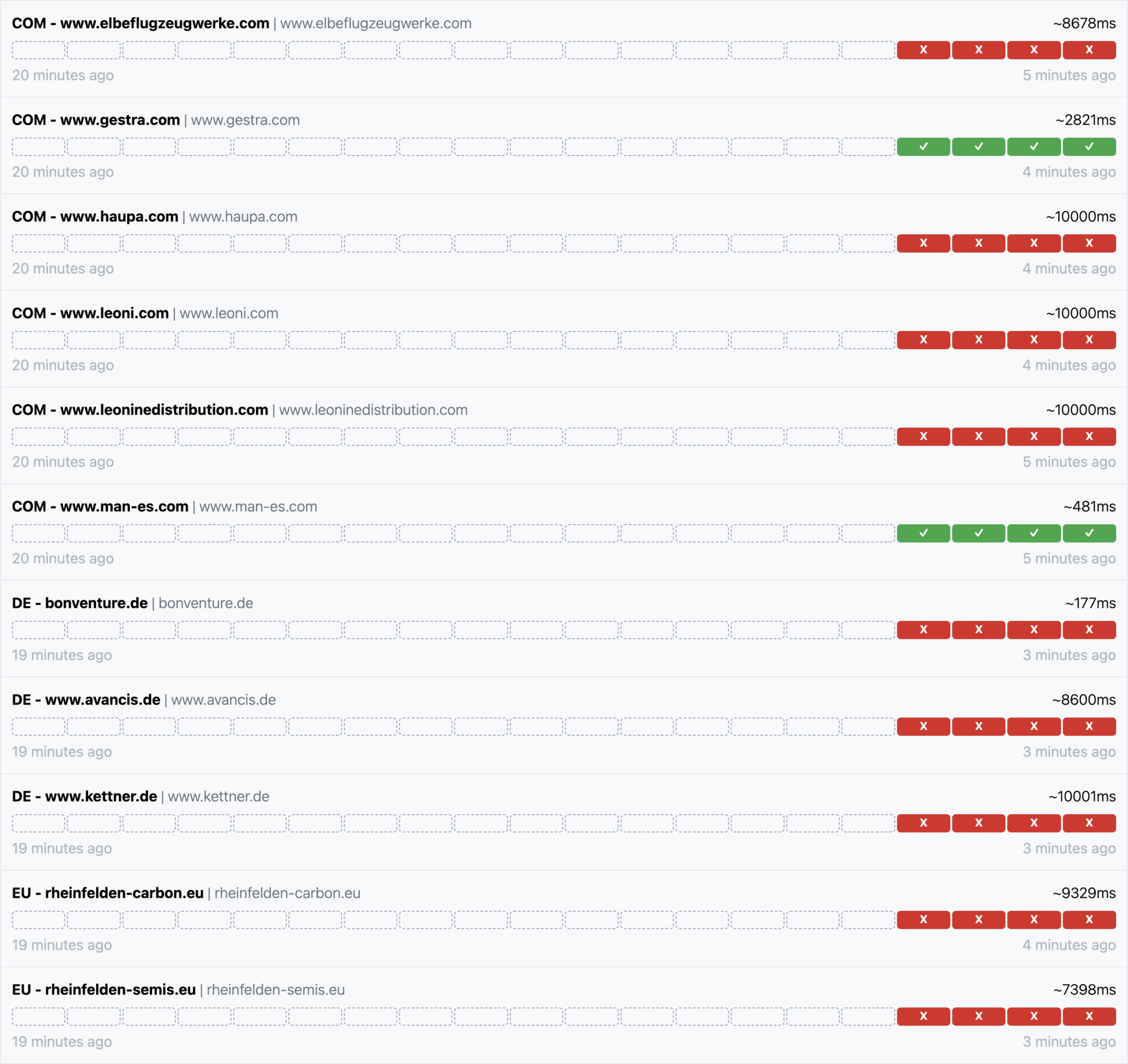
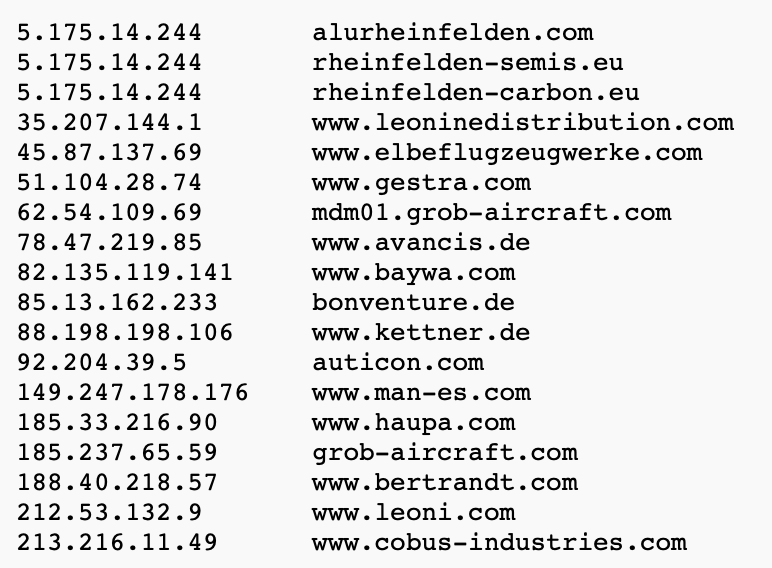
I've been working on an automated triager for the frequent volumetric DDOS we see against www.bbc.com & www.bbc.co.uk.
The idea is to use our edge access logs (stored in BigQuery) to isolate & describe the attack traffic then recommend any additional mitigations/filters etc. It also gives us a database of DDOS metrics/sources we can reference.
Obviously I had to add the obligatory pew-pew map.